@george1421 thanks you george, i will try this tomrrow as i have a pc that needs doing so this is a good test
so the windows driver packs are different from the winPE drivers?
@george1421 thanks you george, i will try this tomrrow as i have a pc that needs doing so this is a good test
so the windows driver packs are different from the winPE drivers?
@george1421
images
├─/drivers
├─z2
├─win10
└─x64
So under the x64 folder do I put the inf files straight in there
do I do this as well after I drop the inf files
pnputil.exe /add-driver “C:\Drivers*.inf” /subdirs /install
@george1421 atm i dont do an unattended xml file as i havnt got a volume license for windows 10, atm when i run sysprep, i do
sysprep /oobe /generalize /shutdown
so do i miss the sections
fog.updateunattend and
Unattend.xml
i imagine i do?
where do i put the .inf driver for my network card then, do i put it here
/images
├─/drivers
├─z2
├─win10
└─x64
obviously i will get the right folder names
@george1421 so reading from this
i miss this out as i dont to unnatended installs
fog.updateunattend
i think i dont anyway?
when you say
Unattend.xml
For WIN10 you must update the unattend.xml file to include this section. This is an example for the amd64 arch.
where is the unattended.xml ?
@george1421 when you say this
So you can either preload the drivers into your golden image before you sysprep it
do you mean download and copy the drivers somewhere on the c drive before i sysprep?
@george1421 how do i configure a post install script @george1421
sorry for the delay, i wasnt notified of your reply, my bad
hi all,
on some machines (mainly hp z workstations) after i deploy a syspreped image of windows 10, i need to install the built in intel driver, this is weird as i can pxe boot into the fog server to deploy the image
i get around installing the intel driver by a usb ethernet adpater as that doesnt require any drivers
thanks,
rob
@george1421 the good thing is, you only need to do the reg hack and app removal on the GI, once you sysprep the GI and capture it, when you deploy it, you have to do nothing and you can deploy to multiple laptops, vms etc
the pic i shows you shows a laptop with TPM enabled, using the deployed image
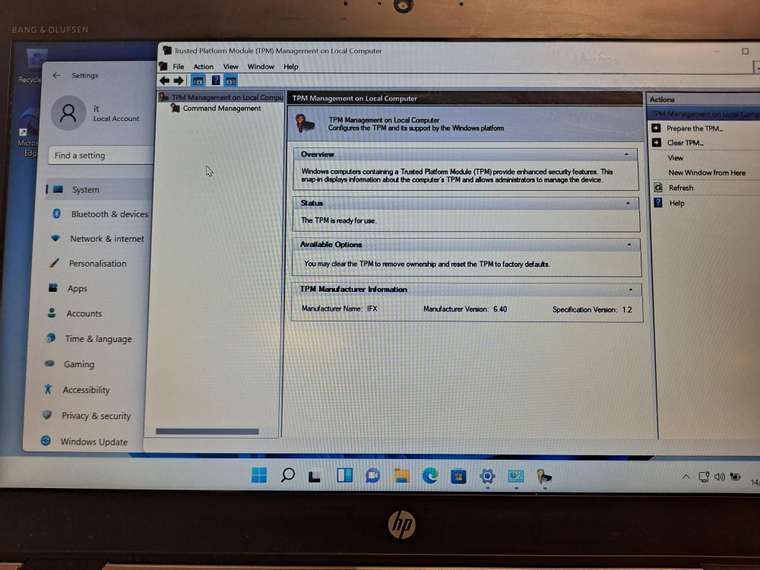
@robertkwild good news, its worked!
before i did “quick inventroy” it listed the vm in “hosts” and then i clicked on “capture” to the image i just created, i used the “windows 10” as the os drop down
i syspreped windows 11, it failed first time, due to some program stopping it, all i had to do was remove it in powershell
Get-AppxPackage Microsoft.BingNews* | Remove-AppxPackage
then try again
sysprep /oobe /generalize /shutdown
it captured it fine, then i deleted that vm, created a new vm, disabled “secure boot”, network booted to my fog clicked on “deploy image” chose the windows 11 image
and the end result i get a nice windows 11 vm desktop 
@robertkwild this is interesting, that key is no longer there, i rebooted to see if it would still boot in windows and it has
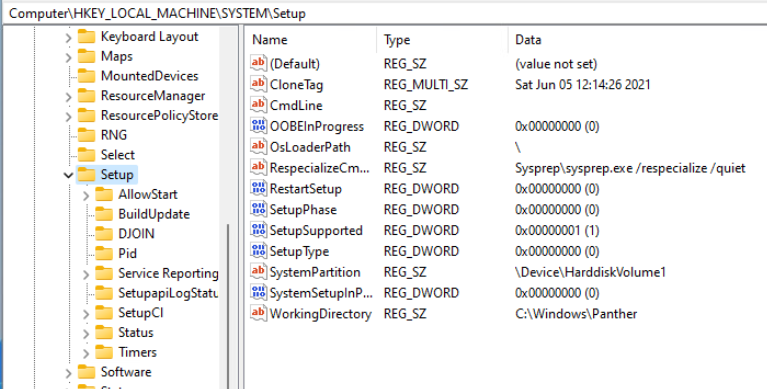
hi all,
got a good way installing windows 11 on esxi, bypassing tpm check, as thats where i got the error saying “your pc doesnt meet all the requirements”
ive also on the vm disabled/unticked “secure boot” so i can still network boot my fog server
heres the how to
https://www.virten.net/2021/10/windows-11-on-vmware-esxi-this-pc-cant-run-windows-11/
basically, when you come to the “enter your key screen” press shift+f10
REG ADD HKLM\SYSTEM\Setup\LabConfig /v BypassTPMCheck /t REG_DWORD /d 1
my end goal is to sysprep it and capture it to fog and then see if i can deploy it to new vm!
thanks,
rob
@george1421 i downloaded the dvd iso instead and followed your awesome guide into how to pxe boot into debian 11.2 and it works!!!
im going to create another menu with a kickstart option like i did with my normal centos 7 2009 one with a normal boot and one with a kickstart file
thanks George again, you rock
@george1421 cool, im going to download this one
https://cdimage.debian.org/debian-cd/current/amd64/iso-cd/debian-11.2.0-amd64-netinst.iso
will this require internet to install as i dont want that, i think it doesnt as its the cdrom min install version?
@george1421 thanks george, this is a post i posted on another board about just installing bloody ubuntu with no internet!!!
issue solved, just disabled the NIC on the vm and then it installed no problem
once it installed i enabled the NIC and in netplan i gave it a static ip
this was the problem where it was getting the error
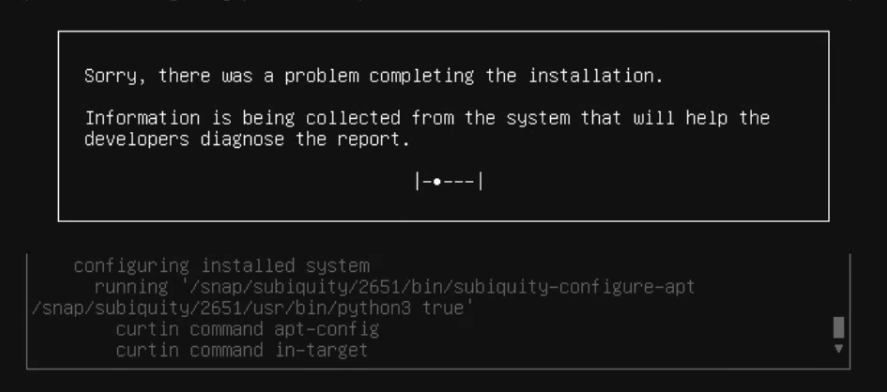
it got stuck or gave me error after curtin
tbh i dont like this new ubuntu aproach ie cloud-init, not impressed
hi all,
trying to get the iso to boot from the ram disk on the client pc but im struggling
im trying this method as ubuntu now uses cloud init instead of the old legacy debian installer
reading this
https://discourse.ubuntu.com/t/netbooting-the-live-server-installer/14510
but theres no link to
so i thought focal would have one but they dont, i just see there legacy images ie debian images
http://archive.ubuntu.com/ubuntu/dists/focal/main/installer-amd64/current/
any help in this would be greatly appreciated
thanks,
rob
@george1421 made it into all one script, even the mkkeys.sh
#!/bin/bash
apt-get update
apt-get upgrade -y
apt-get install -y openssl efitools gnu-efi git build-essential help2man libssl-dev
perl -e'use CPAN; install "File::Slurp"'
mkdir -p /opt/fog/secureboot/efikeys
cat << EOF > /opt/fog/secureboot/mkkeys.sh
#!/bin/bash
# Copyright (c) 2015 by Roderick W. Smith
# Updated 26-Nov-2021 by George1421 for the FOG Project
# Licensed under the terms of the GPL v3
NAME=FOGProjectSB
openssl req -new -x509 -newkey rsa:2048 -subj "/CN=$NAME PK/" -keyout efikeys/PK.key \
-out efikeys/PK.crt -days 3650 -nodes -sha256
openssl req -new -x509 -newkey rsa:2048 -subj "/CN=$NAME KEK/" -keyout efikeys/KEK.key \
-out efikeys/KEK.crt -days 3650 -nodes -sha256
openssl req -new -x509 -newkey rsa:2048 -subj "/CN=$NAME DB/" -keyout efikeys/DB.key \
-out efikeys/DB.crt -days 3650 -nodes -sha256
openssl x509 -in efikeys/PK.crt -out efikeys/PK.cer -outform DER
openssl x509 -in efikeys/KEK.crt -out efikeys/KEK.cer -outform DER
openssl x509 -in efikeys/DB.crt -out efikeys/DB.cer -outform DER
GUID=`python3 -c 'import uuid; print(str(uuid.uuid1()))'`
echo $GUID > efikeys/myGUID.txt
cert-to-efi-sig-list -g $GUID efikeys/PK.crt efikeys/PK.esl
cert-to-efi-sig-list -g $GUID efikeys/KEK.crt efikeys/KEK.esl
cert-to-efi-sig-list -g $GUID efikeys/DB.crt efikeys/DB.esl
rm -f efikeys/noPK.esl
touch efikeys/noPK.esl
sign-efi-sig-list -t "$(date --date='1 second' +'%Y-%m-%d %H:%M:%S')" \
-k efikeys/PK.key -c efikeys/PK.crt PK efikeys/PK.esl efikeys/PK.auth
sign-efi-sig-list -t "$(date --date='1 second' +'%Y-%m-%d %H:%M:%S')" \
-k efikeys/PK.key -c efikeys/PK.crt PK efikeys/noPK.esl efikeys/noPK.auth
sign-efi-sig-list -t "$(date --date='1 second' +'%Y-%m-%d %H:%M:%S')" \
-k efikeys/PK.key -c efikeys/PK.crt KEK efikeys/KEK.esl efikeys/KEK.auth
sign-efi-sig-list -t "$(date --date='1 second' +'%Y-%m-%d %H:%M:%S')" \
-k efikeys/KEK.key -c efikeys/KEK.crt db efikeys/DB.esl efikeys/DB.auth
chmod 0600 efikeys/*.key
echo ""
echo ""
echo "For use with KeyTool, copy the *.auth and *.esl files to a FAT USB"
echo "flash drive or to your EFI System Partition (ESP)."
echo "For use with most UEFIs' built-in key managers, copy the *.cer files;"
echo "but some UEFIs require the *.auth files."
echo ""
EOF
chmod a+x /opt/fog/secureboot/mkkeys.sh
cd /opt/fog/secureboot/
./mkkeys.sh
git clone git://git.kernel.org/pub/scm/linux/kernel/git/jejb/efitools.git
cd /opt/fog/secureboot/efitools
make
mkdir -p /opt/fog/secureboot/hwkeys
cd /opt/fog/secureboot/
efi-readvar -v PK -o /opt/fog/secureboot/hwkeys/hw_PK.esl
efi-readvar -v KEK -o /opt/fog/secureboot/hwkeys/hw_KEK.esl
efi-readvar -v db -o /opt/fog/secureboot/hwkeys/hw_db.esl
efi-readvar -v dbx -o /opt/fog/secureboot/hwkeys/hw_dbx.esl
chmod 666 /opt/fog/secureboot/hwkeys/*
cp /opt/fog/secureboot/efikeys/* /opt/fog/secureboot/efitools/
cp /opt/fog/secureboot/hwkeys/* /opt/fog/secureboot/efitools/
cd /opt/fog/secureboot/efitools
cat hw_db.esl > DB.esl
cat hw_KEK.esl > KEK.esl
cat hw_dbx.esl > dbx.esl
rm LockDown*efi LockDown.so LockDown.o
make
cp LockDown-signed.efi EnrollKeys.efi
mkdir -p /tftpboot
cp /opt/fog/secureboot/efitools/EnrollKeys.efi /tftpboot
mv /var/www/html/fog/service/ipxe/bzImage /var/www/html/fog/service/ipxe/bzImage-unsigned
sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /var/www/html/fog/service/ipxe/bzImage /var/www/html/fog/service/ipxe/bzImage-unsigned
mv /var/www/html/fog/service/ipxe/bzImage32 /var/www/html/fog/service/ipxe/bzImage32-unsigned
sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /var/www/html/fog/service/ipxe/bzImage32 /var/www/html/fog/service/ipxe/bzImage32-unsigned
mv /var/www/html/fog/service/ipxe/refind.efi /var/www/html/fog/service/ipxe/refind-unsigned.efi
sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /var/www/html/fog/service/ipxe/refind.efi /var/www/html/fog/service/ipxe/refind-unsigned.efi
mv /tftpboot/ipxe.efi /tftpboot/ipxe-unsigned.efi
sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /tftpboot/ipxe.efi /tftpboot/ipxe-unsigned.efi
mv /tftpboot/snponly.efi /tftpboot/snponly-unsigned.efi
sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /tftpboot/snponly.efi /tftpboot/snponly-unsigned.efi
mv /tftpboot/snp.efi /tftpboot/snp-unsigned.efi
sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /tftpboot/snp.efi /tftpboot/snp-unsigned.efi
@george1421 thanks George il check my params for the enroll key entry
Just out of interest as I’m making the enrollkeys.efi using another laptop which has a more recent UEFI and secure boot keys, I know I need to export it to my fog server but what about dB.crt and dB.key, do I need to export these aswell to the fog server or can I use the ones already on there on the fog server?
This is because I have followed this howto on both systems, so I have 2 sets of crt and key files one on the fog server and one on the laptop
/opt/fog/secureboot/efitools/EnrollKeys.efi
/opt/fog/secureboot/efikeys/DB.crt
/opt/fog/secureboot/efikeys/DB.key