lovely stuff, job done -
kernel http://fog/listing/centos7_1804/images/pxeboot/vmlinuz ks=http://fog/listing/centos7_1804/ks.cfg
initrd http://fog/listing/centos7_1804/images/pxeboot/initrd.img
boot || goto MENU
lovely stuff, job done -
kernel http://fog/listing/centos7_1804/images/pxeboot/vmlinuz ks=http://fog/listing/centos7_1804/ks.cfg
initrd http://fog/listing/centos7_1804/images/pxeboot/initrd.img
boot || goto MENU
@george1421 made it into all one script, even the mkkeys.sh
#!/bin/bash
apt-get update
apt-get upgrade -y
apt-get install -y openssl efitools gnu-efi git build-essential help2man libssl-dev
perl -e'use CPAN; install "File::Slurp"'
mkdir -p /opt/fog/secureboot/efikeys
cat << EOF > /opt/fog/secureboot/mkkeys.sh
#!/bin/bash
# Copyright (c) 2015 by Roderick W. Smith
# Updated 26-Nov-2021 by George1421 for the FOG Project
# Licensed under the terms of the GPL v3
NAME=FOGProjectSB
openssl req -new -x509 -newkey rsa:2048 -subj "/CN=$NAME PK/" -keyout efikeys/PK.key \
-out efikeys/PK.crt -days 3650 -nodes -sha256
openssl req -new -x509 -newkey rsa:2048 -subj "/CN=$NAME KEK/" -keyout efikeys/KEK.key \
-out efikeys/KEK.crt -days 3650 -nodes -sha256
openssl req -new -x509 -newkey rsa:2048 -subj "/CN=$NAME DB/" -keyout efikeys/DB.key \
-out efikeys/DB.crt -days 3650 -nodes -sha256
openssl x509 -in efikeys/PK.crt -out efikeys/PK.cer -outform DER
openssl x509 -in efikeys/KEK.crt -out efikeys/KEK.cer -outform DER
openssl x509 -in efikeys/DB.crt -out efikeys/DB.cer -outform DER
GUID=`python3 -c 'import uuid; print(str(uuid.uuid1()))'`
echo $GUID > efikeys/myGUID.txt
cert-to-efi-sig-list -g $GUID efikeys/PK.crt efikeys/PK.esl
cert-to-efi-sig-list -g $GUID efikeys/KEK.crt efikeys/KEK.esl
cert-to-efi-sig-list -g $GUID efikeys/DB.crt efikeys/DB.esl
rm -f efikeys/noPK.esl
touch efikeys/noPK.esl
sign-efi-sig-list -t "$(date --date='1 second' +'%Y-%m-%d %H:%M:%S')" \
-k efikeys/PK.key -c efikeys/PK.crt PK efikeys/PK.esl efikeys/PK.auth
sign-efi-sig-list -t "$(date --date='1 second' +'%Y-%m-%d %H:%M:%S')" \
-k efikeys/PK.key -c efikeys/PK.crt PK efikeys/noPK.esl efikeys/noPK.auth
sign-efi-sig-list -t "$(date --date='1 second' +'%Y-%m-%d %H:%M:%S')" \
-k efikeys/PK.key -c efikeys/PK.crt KEK efikeys/KEK.esl efikeys/KEK.auth
sign-efi-sig-list -t "$(date --date='1 second' +'%Y-%m-%d %H:%M:%S')" \
-k efikeys/KEK.key -c efikeys/KEK.crt db efikeys/DB.esl efikeys/DB.auth
chmod 0600 efikeys/*.key
echo ""
echo ""
echo "For use with KeyTool, copy the *.auth and *.esl files to a FAT USB"
echo "flash drive or to your EFI System Partition (ESP)."
echo "For use with most UEFIs' built-in key managers, copy the *.cer files;"
echo "but some UEFIs require the *.auth files."
echo ""
EOF
chmod a+x /opt/fog/secureboot/mkkeys.sh
cd /opt/fog/secureboot/
./mkkeys.sh
git clone git://git.kernel.org/pub/scm/linux/kernel/git/jejb/efitools.git
cd /opt/fog/secureboot/efitools
make
mkdir -p /opt/fog/secureboot/hwkeys
cd /opt/fog/secureboot/
efi-readvar -v PK -o /opt/fog/secureboot/hwkeys/hw_PK.esl
efi-readvar -v KEK -o /opt/fog/secureboot/hwkeys/hw_KEK.esl
efi-readvar -v db -o /opt/fog/secureboot/hwkeys/hw_db.esl
efi-readvar -v dbx -o /opt/fog/secureboot/hwkeys/hw_dbx.esl
chmod 666 /opt/fog/secureboot/hwkeys/*
cp /opt/fog/secureboot/efikeys/* /opt/fog/secureboot/efitools/
cp /opt/fog/secureboot/hwkeys/* /opt/fog/secureboot/efitools/
cd /opt/fog/secureboot/efitools
cat hw_db.esl > DB.esl
cat hw_KEK.esl > KEK.esl
cat hw_dbx.esl > dbx.esl
rm LockDown*efi LockDown.so LockDown.o
make
cp LockDown-signed.efi EnrollKeys.efi
mkdir -p /tftpboot
cp /opt/fog/secureboot/efitools/EnrollKeys.efi /tftpboot
mv /var/www/html/fog/service/ipxe/bzImage /var/www/html/fog/service/ipxe/bzImage-unsigned
sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /var/www/html/fog/service/ipxe/bzImage /var/www/html/fog/service/ipxe/bzImage-unsigned
mv /var/www/html/fog/service/ipxe/bzImage32 /var/www/html/fog/service/ipxe/bzImage32-unsigned
sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /var/www/html/fog/service/ipxe/bzImage32 /var/www/html/fog/service/ipxe/bzImage32-unsigned
mv /var/www/html/fog/service/ipxe/refind.efi /var/www/html/fog/service/ipxe/refind-unsigned.efi
sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /var/www/html/fog/service/ipxe/refind.efi /var/www/html/fog/service/ipxe/refind-unsigned.efi
mv /tftpboot/ipxe.efi /tftpboot/ipxe-unsigned.efi
sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /tftpboot/ipxe.efi /tftpboot/ipxe-unsigned.efi
mv /tftpboot/snponly.efi /tftpboot/snponly-unsigned.efi
sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /tftpboot/snponly.efi /tftpboot/snponly-unsigned.efi
mv /tftpboot/snp.efi /tftpboot/snp-unsigned.efi
sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /tftpboot/snp.efi /tftpboot/snp-unsigned.efi
@robertkwild good news, its worked!
before i did “quick inventroy” it listed the vm in “hosts” and then i clicked on “capture” to the image i just created, i used the “windows 10” as the os drop down
i syspreped windows 11, it failed first time, due to some program stopping it, all i had to do was remove it in powershell
Get-AppxPackage Microsoft.BingNews* | Remove-AppxPackage
then try again
sysprep /oobe /generalize /shutdown
it captured it fine, then i deleted that vm, created a new vm, disabled “secure boot”, network booted to my fog clicked on “deploy image” chose the windows 11 image
and the end result i get a nice windows 11 vm desktop 
@AlexPDX @Sebastian-Roth it was something simple in the end
BIOS > advanced > system options
i turned off/unticked - configure storage controller for VMD
basically its there version of RAID, untick it and its AHCI
hi all,
got a good way installing windows 11 on esxi, bypassing tpm check, as thats where i got the error saying “your pc doesnt meet all the requirements”
ive also on the vm disabled/unticked “secure boot” so i can still network boot my fog server
heres the how to
https://www.virten.net/2021/10/windows-11-on-vmware-esxi-this-pc-cant-run-windows-11/
basically, when you come to the “enter your key screen” press shift+f10
REG ADD HKLM\SYSTEM\Setup\LabConfig /v BypassTPMCheck /t REG_DWORD /d 1
my end goal is to sysprep it and capture it to fog and then see if i can deploy it to new vm!
thanks,
rob
@george1421 result!!!
i bought a HP NIC as i have a HP laptop and it works
this one if anyone is inteerested
https://www.amazon.co.uk/HP-N7P47AA-Network-DesignJet-Adapters-Black/dp/B01618WGMY?th=1
as literally star tech, ugreen, tp link, realtek or asix chipsets didnt work
@george1421 the good thing is, you only need to do the reg hack and app removal on the GI, once you sysprep the GI and capture it, when you deploy it, you have to do nothing and you can deploy to multiple laptops, vms etc
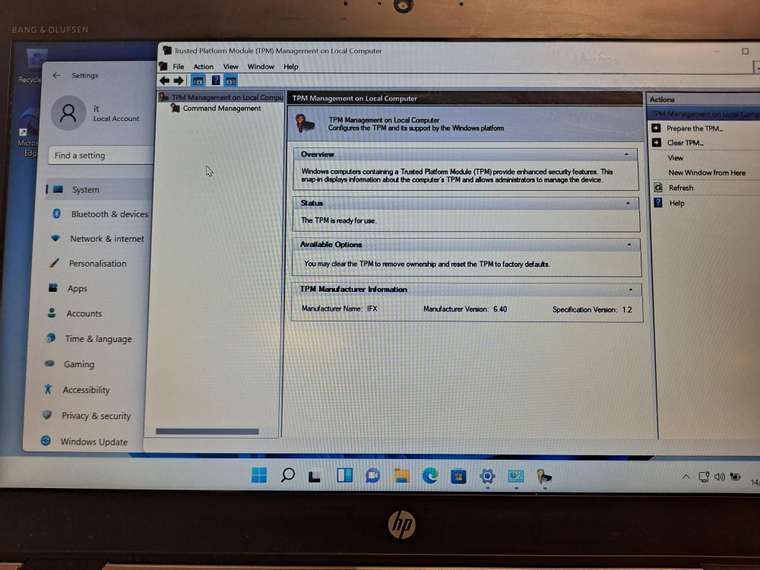
the pic i shows you shows a laptop with TPM enabled, using the deployed image
@Tom-Elliott sorry took my time in replying back tom my bad
in the end i updated my stable to the latest 1.5.10.1650 and now when i capture the image it saves it as a folder not a file
@tcthorne i thought i resolved it by updating fog to 1.5.10.1650 ie the latest at the time but guess what the error has come back and i have no idea why its come back, the last resort is to update to working branch ie 1.6
ok scrap the local GPO done this and it works
reg add HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce /v firstlogon /t REG_SZ /d powershell -noexit -ep bypass c:\users\admin\sysprep\firstlogon.ps1 /f
solved…
i used a computer startup script
script name:
C:\Users\admin\sysprep\firstlogon.ps1
script parameters:
powershell -ep Bypass
and heres the script (just made a rough one to test and every command ran as when i logged in after the pc syspreped all commands worked)
start-process 'C:\Users\admin\sysprep\Firefox Setup 138.0.exe' /S -wait
Remove-ItemProperty -Path "HKLM:\SOFTWARE\Wow6432Node\AdventNet\DesktopCentral\DCAgent\" -Name "ImagedComputer" -Force
Remove-Item -Path "HKLM:\SOFTWARE\Wow6432Node\AdventNet\DesktopCentral\DCAgent\SystemDetails" -Force
Set-LocalUser -Name "user01" -PasswordNeverExpires $true
Set-LocalUser -Name "it" -PasswordNeverExpires $true
remove-item -path C:\Users\admin\sysprep -recurse -force
@rodluz thanks but doesnt this need a VL key to run those scripts?
ok ive done this and it works
<component name="Microsoft-Windows-Deployment" processorArchitecture="amd64" publicKeyToken="31bf3856ad364e35" language="neutral" versionScope="NonSxS" xmlns:wcm="http://schemas.microsoft.com/WMIConfig/2002/State" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<RunSynchronous>
<RunSynchronousCommand wcm:action="add">
<Description>firstlogon</Description>
<Order>1</Order>
<Path>C:\Users\admin\sysprep\firstlogon.bat</Path>
</RunSynchronousCommand>
</RunSynchronous>
</component>
and my bat is just this
@echo off
C:\Users\admin\sysprep\SophosSetup.exe --quiet
rmdir /Q /S C:\Users\admin\sysprep
this works but when i try to run a powershell command that needs admin it cant do it ie
powershell.exe -ExecutionPolicy Bypass -File path-to-ps1
in there i just have this
Set-LocalUser -Name “user” -PasswordNeverExpires $true
but everytime after the sysprep and it loads into windows it hasnt done it as it hasnt got admin privs
so how come cmd had admin but ps1 doesnt?
any idea please
thanks,
rob
hi all,
turned off “secure boot” obviously to use fog to deploy a image to a pc after windows is installed turned back on “secure boot” but now windows cant boot and going into automatic repair mode and cant boot windows
is there anyway to turn on secure boot after windows and windows still works?
thanks,
rob
@Tom-Elliott is there a way to find out where its failing
i have the PCAP file if interested?
@Tom-Elliott thanks, now i know the “autoexec.ipxe…not found” is fine its just a warning and it ignores it and continues
but why then does this laptop fail to boot into fog and a vm does boot into fog?
is it because the laptop uses a usb/ethernet adapter
that didnt work, changed to “snponly.efi” but still same error about autoexec.ipxe
but when i do a ls on /tftpboot i cant see “autoexec.ipxe” is this why
ls -lah /tftpboot
total 7.0M
drwxr-xr-x 5 fogproject root 4.0K Apr 23 14:22 .
dr-xr-xr-x. 22 root root 4.0K Apr 23 13:48 …
drwxr-xr-x 4 fogproject root 4.0K Apr 12 12:47 10secdelay
drwxr-xr-x 2 fogproject root 118 Apr 12 12:47 arm64-efi
-rw-r-xr-x 1 fogproject root 479 Apr 23 13:58 default.ipxe
drwxr-xr-x 2 fogproject root 118 Apr 12 12:47 i386-efi
-rw-r-xr-x 1 fogproject root 326K Apr 23 13:58 intel.efi
-rw-r-xr-x 1 fogproject root 120K Apr 23 13:58 intel.kkpxe
-rw-r-xr-x 1 fogproject root 120K Apr 23 13:58 intel.kpxe
-rw-r-xr-x 1 fogproject root 120K Apr 23 13:58 intel.pxe
-rw-r-xr-x 1 fogproject root 1.2M Apr 23 13:58 ipxe.efi
-rw-r-xr-x 1 fogproject root 1.0M Apr 23 13:58 ipxe.iso
-rw-r-xr-x 1 fogproject root 383K Apr 23 13:58 ipxe.kkpxe
-rw-r-xr-x 1 fogproject root 383K Apr 23 13:58 ipxe.kpxe
-rw-r-xr-x 1 fogproject root 382K Apr 23 13:58 ipxe.krn
-rw-r-xr-x 1 fogproject root 382K Apr 23 13:58 ipxe.lkrn
-rw-r-xr-x 1 fogproject root 383K Apr 23 13:58 ipxe.pxe
-rw-r-xr-x 1 fogproject root 400K Apr 23 13:58 ipxe.usb
-rw-r-xr-x 1 fogproject root 26K Apr 23 13:58 memdisk
-rw-r-xr-x 1 fogproject root 325K Apr 23 13:58 ncm–ecm–axge.efi
-rw-r-xr-x 1 fogproject root 325K Apr 23 13:58 realtek.efi
-rw-r-xr-x 1 fogproject root 121K Apr 23 13:58 realtek.kkpxe
-rw-r-xr-x 1 fogproject root 121K Apr 23 13:58 realtek.kpxe
-rw-r-xr-x 1 fogproject root 121K Apr 23 13:58 realtek.pxe
-rw-r-xr-x 1 fogproject root 325K Apr 23 13:58 snp.efi
-rw-r-xr-x 1 fogproject root 325K Apr 23 13:58 snponly.efi
-rw-r-xr-x 1 fogproject root 120K Apr 23 13:58 undionly.kkpxe
-rw-r-xr-x 1 fogproject root 120K Apr 23 13:58 undionly.kpxe
-rw-r-xr-x 1 fogproject root 120K Apr 23 13:58 undionly.pxe
is it because i havnt got a dns entry for fog since i changed to using https?
what is interesting is that fog works on a vm ie it says “autoexec.ipxe” not found and it continues to load the fog menu where i can deploy my image
so its only happening on new uefi firmware looks like it
hi all,
when i installed fog for the first time on a new OS alma 9.5 (old fog was on centos 7) i turned on https but now my clients cant connect to fog, they get this

i think this is happening because i enabled https, is there anyway to turn it off or am i stuck with it on
thanks,
rob
hi all,
I copied my image from old fog server to new fog server via rsync -a, I also created a new image on the web portal and i can successfully deploy it to a new pc but on the web portal it doesnt specify the size
anyway i can do this please as in terminal when i do a du on the image i get the size 15G
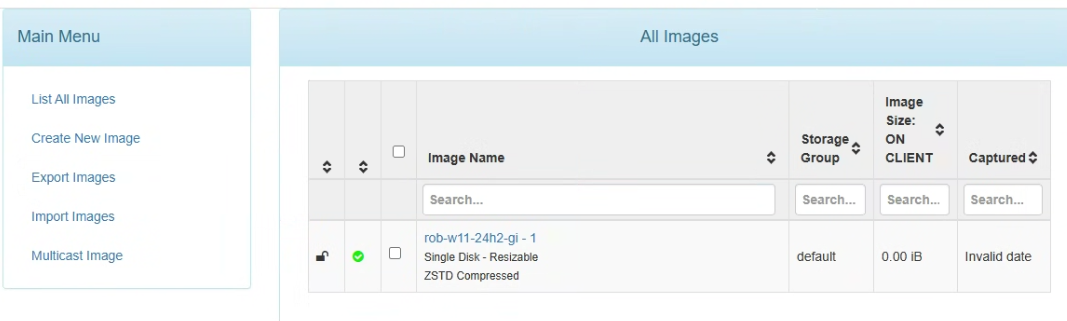
thanks,
rob