powershell snapin no output, non error
-
When I configured the snapin with my example script that installs the FogApi Module and runs the universal command with the snapin setup with “powershell x64” like this
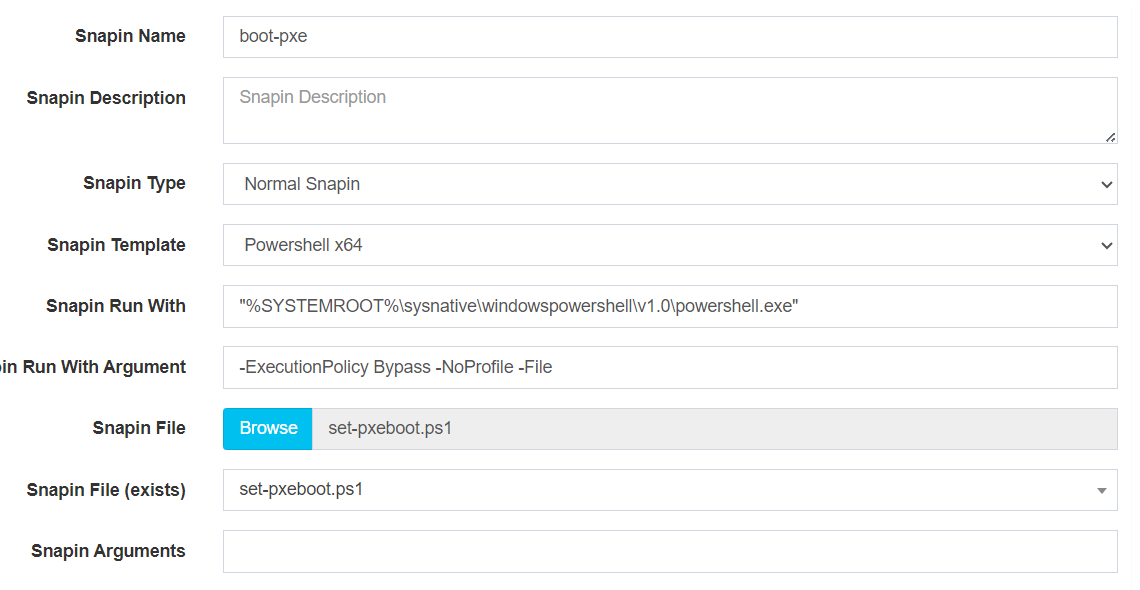
The snapin worked as expected and the host boots to pxe. I only tested this snapin method on a VM so far but I imagine it will work beyond that.
-
 J JJ Fullmer referenced this topic on
J JJ Fullmer referenced this topic on