secure boot - dbx.esl no such file to move
-
hi all,
im following this guide
https://forums.fogproject.org/topic/15888/imaging-with-fog-and-secure-boot-poc/3
but getting stuck at below
mv dbx.esl dbx-fog.esl mv: cannot stat 'dbx.esl': No such file or directory root@rkw-Venue-11-Pro-7140:/opt/fog/secureboot/efitools# ls cert-to-efi-hash-list DB2-pkupdate.auth efi-updatevar hw_db.esl KeyTool-signed.efi ms-kek.crt PK.esl ShimReplace-signed.efi cert-to-efi-hash-list.c DB2-update.auth efi-updatevar.c hw_dbx.esl KeyTool.so ms-kek-hash-blacklist.auth PK.h ShimReplace.so cert-to-efi-hash-list.o DB.auth efi-updatevar.o hw_KEK.esl lib ms-kek-pkupdate.auth PK-hash-blacklist.auth sig-list-to-certs cert-to-efi-sig-list DB-blacklist.auth flash-var hw_PK.esl Loader.c ms-kek-update.auth PK.key sig-list-to-certs.c cert-to-efi-sig-list.c DB.cer flash-var.c include Loader.efi ms-uefi.auth PK-pkupdate.auth sig-list-to-certs.o cert-to-efi-sig-list.o DB.crt flash-var.o KEK.auth Loader-signed.efi ms-uefi-blacklist.auth PK-update.auth sign-efi-sig-list COPYING DB-fog.esl hash-to-efi-sig-list KEK-blacklist.auth Loader.so ms-uefi.crt PreLoader.c sign-efi-sig-list.c DB1.auth DB.h hash-to-efi-sig-list.c KEK.cer LockDown.c ms-uefi-hash-blacklist.auth README sign-efi-sig-list.o DB1-blacklist.auth DB-hash-blacklist.auth hash-to-efi-sig-list.o KEK.crt LockDown.efi ms-uefi-pkupdate.auth ReadVars.c UpdateVars.c DB1-hash-blacklist.auth DB.key HashTool.c KEK-fog.esl LockDown.o ms-uefi-update.auth ReadVars.efi UpdateVars.efi DB1.key DB-pkupdate.auth HashTool.efi KEK.h LockDown-signed.efi myGUID.txt ReadVars-signed.efi UpdateVars-signed.efi DB1-pkupdate.auth DB-update.auth HashTool-signed.efi KEK-hash-blacklist.auth LockDown.so noPK.auth ReadVars.so UpdateVars.so DB1-update.auth doc HashTool.so KEK.key Makefile noPK.esl SetNull.c xxdi.pl DB2.auth efi-keytool.c HelloWorld.c KEK-pkupdate.auth Make.rules PK.auth SetNull.efi DB2-blacklist.auth efi-readvar HelloWorld.efi KEK-update.auth mkusb.sh PK-blacklist.auth SetNull-signed.efi DB2-hash-blacklist.auth efi-readvar.c HelloWorld-signed.efi KeyTool.c ms-kek.auth PK.cer ShimReplace.c DB2.key efi-readvar.o HelloWorld.so KeyTool.efi ms-kek-blacklist.auth PK.crt ShimReplace.efi root@rkw-Venue-11-Pro-7140:/opt/fog/secureboot/efitools#can i manually put a dbx.esl in there, if so has anyone got the file i could drop in here
thanks,
rob -
@robertkwild Since you didn’t reference a step I can only guess at the answer.
But the dbx.esl is created on this post Preparing the FOG server with the prerequisites
More specifically is a copy of the dbx file you exported out of hardware in this section
sudo efi-readvar -v dbx -o /opt/fog/secureboot/hwkeys/hw_dbx.esldbx.esl is also created when you run these commands
cd /opt/fog/secureboot/efitools makeThis is when you first compile the efitools programs
Then we rename the first compiled version with this command because we don’t need it in the finished product. We’ll use the hw one that was downloaded from the firmware.mv dbx.esl dbx-fog.eslAnd then finally we take the firmware hw_dbx.esl file and copy it over to the dbx.esl file name.
cat hw_dbx.esl > dbx.eslDepending on where you are getting the error I think you missed a step. The dbx.esl file contains any certificates that have been revoked. When you compile the file signing keys the default microsoft dbx.esl file is good enough.
-
sudo efi-readvar -v dbx -o /opt/fog/secureboot/hwkeys/hw_dbx.eslI did run this command and then I moved it to this dir as you can see from my previous post when I ran the ls command
I did run the make command in the efitools dir but as you can see it’s not here as I’ve done an ls command and it’s not listed
I can’t mv dbx.esl as it’s not there to move
I can however cp hw_dbx.esl and rename the copy dbx.esl so I do have a dbx.esl file, do I have to do this?
Thanks
Rob -
@robertkwild said in secure boot - dbx.esl no such file to move:
I can’t mv dbx.esl as it’s not there to move
So if after you compile efitools and the dbx.esl doesn’t exist that is OK since you will be replacing it with the exported
hw_dbx.eslkey. So its all good -
@george1421 thank you george very much
im doing this on another laptop with secure boot on and then il transfer the files to my fog server that way
is the below file the only file i need from the laptop, or do i need these two files aswell
/opt/fog/secureboot/efitools/EnrollKeys.efi
/opt/fog/secureboot/efikeys/DB.crt
/opt/fog/secureboot/efikeys/DB.keythanks,
rob -
@robertkwild If you are going to let EnrollKeys.efi update your PC then that is the only thing you need for pxe booting
You need to sign ipxe.efi and bzImage using the other keys. But that all stays on the FOG server.
-
@george1421 thanks
also im using as the boot file name “snp.efi” is that a problem
-
@robertkwild said in secure boot - dbx.esl no such file to move:
boot file name “snp.efi”
Not a problem as long as you sign that file too. Any efi file you want to boot needs to be signed with the matching certificate in firmware.
-
@george1421 so your saying
mv /tftpboot/ipxe.efi /tftpboot/ipxe-unsigned.efi sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /tftpboot/ipxe.efi /tftpboot/ipxe-unsigned.efii could all instances of “ipxe.efi” with any one of these
intel.efi
ipxe.efi
realtek.efi
snp.efi
snponly.efithanks,
rob -
@george1421 i get this error
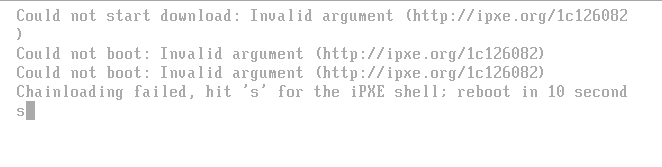
-
@robertkwild What does your parameter block look for this menu item?
It should be similar to this if the error was generated when applying the enrollkeys.efi program.
chain tftp:/${fog-ip}/EnrollKeys.efi echo Rebooting the system in 8 seconds sleep 5 reboot -
@george1421 thanks George il check my params for the enroll key entry
Just out of interest as I’m making the enrollkeys.efi using another laptop which has a more recent UEFI and secure boot keys, I know I need to export it to my fog server but what about dB.crt and dB.key, do I need to export these aswell to the fog server or can I use the ones already on there on the fog server?
This is because I have followed this howto on both systems, so I have 2 sets of crt and key files one on the fog server and one on the laptop
/opt/fog/secureboot/efitools/EnrollKeys.efi
/opt/fog/secureboot/efikeys/DB.crt
/opt/fog/secureboot/efikeys/DB.key -
@george1421 made it into all one script, even the mkkeys.sh
#!/bin/bash apt-get update apt-get upgrade -y apt-get install -y openssl efitools gnu-efi git build-essential help2man libssl-dev perl -e'use CPAN; install "File::Slurp"' mkdir -p /opt/fog/secureboot/efikeys cat << EOF > /opt/fog/secureboot/mkkeys.sh #!/bin/bash # Copyright (c) 2015 by Roderick W. Smith # Updated 26-Nov-2021 by George1421 for the FOG Project # Licensed under the terms of the GPL v3 NAME=FOGProjectSB openssl req -new -x509 -newkey rsa:2048 -subj "/CN=$NAME PK/" -keyout efikeys/PK.key \ -out efikeys/PK.crt -days 3650 -nodes -sha256 openssl req -new -x509 -newkey rsa:2048 -subj "/CN=$NAME KEK/" -keyout efikeys/KEK.key \ -out efikeys/KEK.crt -days 3650 -nodes -sha256 openssl req -new -x509 -newkey rsa:2048 -subj "/CN=$NAME DB/" -keyout efikeys/DB.key \ -out efikeys/DB.crt -days 3650 -nodes -sha256 openssl x509 -in efikeys/PK.crt -out efikeys/PK.cer -outform DER openssl x509 -in efikeys/KEK.crt -out efikeys/KEK.cer -outform DER openssl x509 -in efikeys/DB.crt -out efikeys/DB.cer -outform DER GUID=`python3 -c 'import uuid; print(str(uuid.uuid1()))'` echo $GUID > efikeys/myGUID.txt cert-to-efi-sig-list -g $GUID efikeys/PK.crt efikeys/PK.esl cert-to-efi-sig-list -g $GUID efikeys/KEK.crt efikeys/KEK.esl cert-to-efi-sig-list -g $GUID efikeys/DB.crt efikeys/DB.esl rm -f efikeys/noPK.esl touch efikeys/noPK.esl sign-efi-sig-list -t "$(date --date='1 second' +'%Y-%m-%d %H:%M:%S')" \ -k efikeys/PK.key -c efikeys/PK.crt PK efikeys/PK.esl efikeys/PK.auth sign-efi-sig-list -t "$(date --date='1 second' +'%Y-%m-%d %H:%M:%S')" \ -k efikeys/PK.key -c efikeys/PK.crt PK efikeys/noPK.esl efikeys/noPK.auth sign-efi-sig-list -t "$(date --date='1 second' +'%Y-%m-%d %H:%M:%S')" \ -k efikeys/PK.key -c efikeys/PK.crt KEK efikeys/KEK.esl efikeys/KEK.auth sign-efi-sig-list -t "$(date --date='1 second' +'%Y-%m-%d %H:%M:%S')" \ -k efikeys/KEK.key -c efikeys/KEK.crt db efikeys/DB.esl efikeys/DB.auth chmod 0600 efikeys/*.key echo "" echo "" echo "For use with KeyTool, copy the *.auth and *.esl files to a FAT USB" echo "flash drive or to your EFI System Partition (ESP)." echo "For use with most UEFIs' built-in key managers, copy the *.cer files;" echo "but some UEFIs require the *.auth files." echo "" EOF chmod a+x /opt/fog/secureboot/mkkeys.sh cd /opt/fog/secureboot/ ./mkkeys.sh git clone git://git.kernel.org/pub/scm/linux/kernel/git/jejb/efitools.git cd /opt/fog/secureboot/efitools make mkdir -p /opt/fog/secureboot/hwkeys cd /opt/fog/secureboot/ efi-readvar -v PK -o /opt/fog/secureboot/hwkeys/hw_PK.esl efi-readvar -v KEK -o /opt/fog/secureboot/hwkeys/hw_KEK.esl efi-readvar -v db -o /opt/fog/secureboot/hwkeys/hw_db.esl efi-readvar -v dbx -o /opt/fog/secureboot/hwkeys/hw_dbx.esl chmod 666 /opt/fog/secureboot/hwkeys/* cp /opt/fog/secureboot/efikeys/* /opt/fog/secureboot/efitools/ cp /opt/fog/secureboot/hwkeys/* /opt/fog/secureboot/efitools/ cd /opt/fog/secureboot/efitools cat hw_db.esl > DB.esl cat hw_KEK.esl > KEK.esl cat hw_dbx.esl > dbx.esl rm LockDown*efi LockDown.so LockDown.o make cp LockDown-signed.efi EnrollKeys.efi mkdir -p /tftpboot cp /opt/fog/secureboot/efitools/EnrollKeys.efi /tftpboot mv /var/www/html/fog/service/ipxe/bzImage /var/www/html/fog/service/ipxe/bzImage-unsigned sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /var/www/html/fog/service/ipxe/bzImage /var/www/html/fog/service/ipxe/bzImage-unsigned mv /var/www/html/fog/service/ipxe/bzImage32 /var/www/html/fog/service/ipxe/bzImage32-unsigned sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /var/www/html/fog/service/ipxe/bzImage32 /var/www/html/fog/service/ipxe/bzImage32-unsigned mv /var/www/html/fog/service/ipxe/refind.efi /var/www/html/fog/service/ipxe/refind-unsigned.efi sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /var/www/html/fog/service/ipxe/refind.efi /var/www/html/fog/service/ipxe/refind-unsigned.efi mv /tftpboot/ipxe.efi /tftpboot/ipxe-unsigned.efi sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /tftpboot/ipxe.efi /tftpboot/ipxe-unsigned.efi mv /tftpboot/snponly.efi /tftpboot/snponly-unsigned.efi sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /tftpboot/snponly.efi /tftpboot/snponly-unsigned.efi mv /tftpboot/snp.efi /tftpboot/snp-unsigned.efi sbsign --key /opt/fog/secureboot/efikeys/DB.key --cert /opt/fog/secureboot/efikeys/DB.crt --output /tftpboot/snp.efi /tftpboot/snp-unsigned.efi -
P pocca referenced this topic on