How do I get dnsmasq to direct PXE to my fogserver IP instead of my dnsmasq server IP?
-
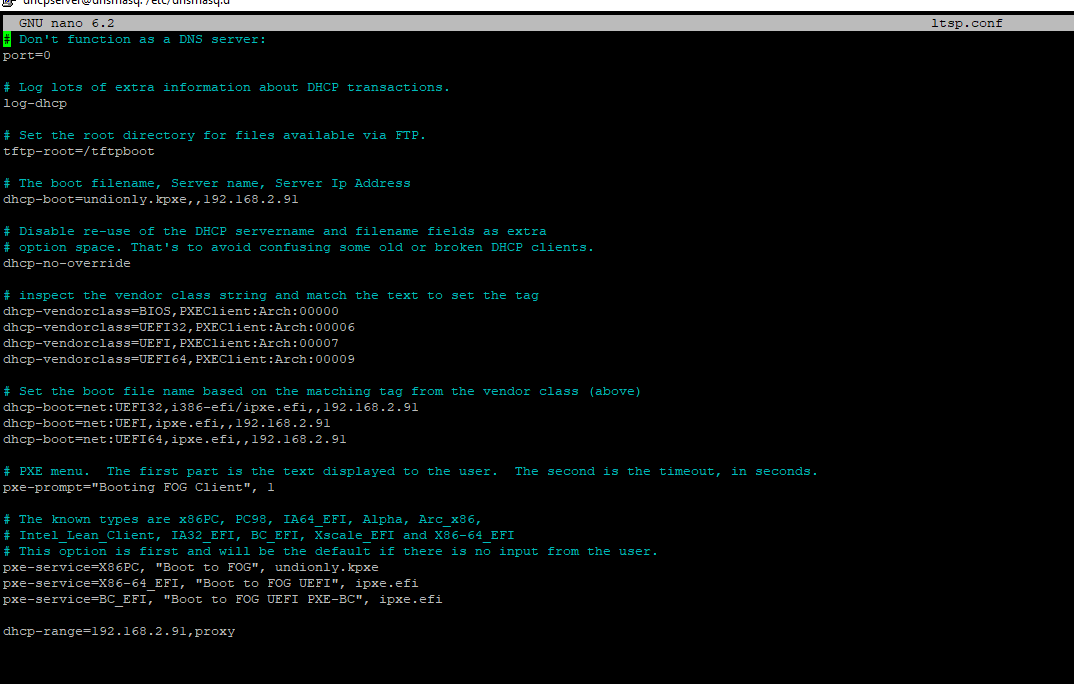
Here is the contents of my ltsp file in my dnsmasq.d directory.
My fog server IP is 192.168.2.91
The IP the VM dnsmasq is being hosted on is 192.168.2.120
Is there a second file that needs to be made or deleted in the VM that is hosting the dnsmasq service?
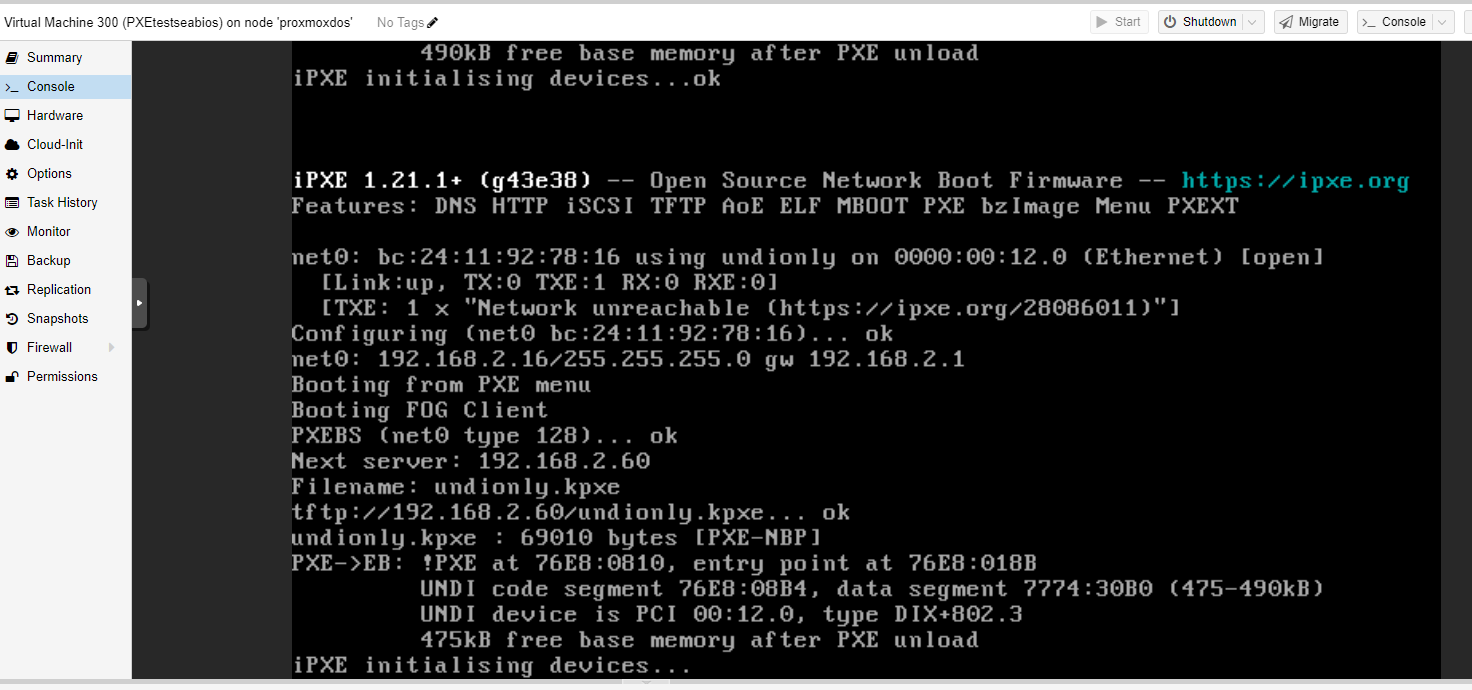
When I try to boot to pxe with what I currently have pxe is constantly looping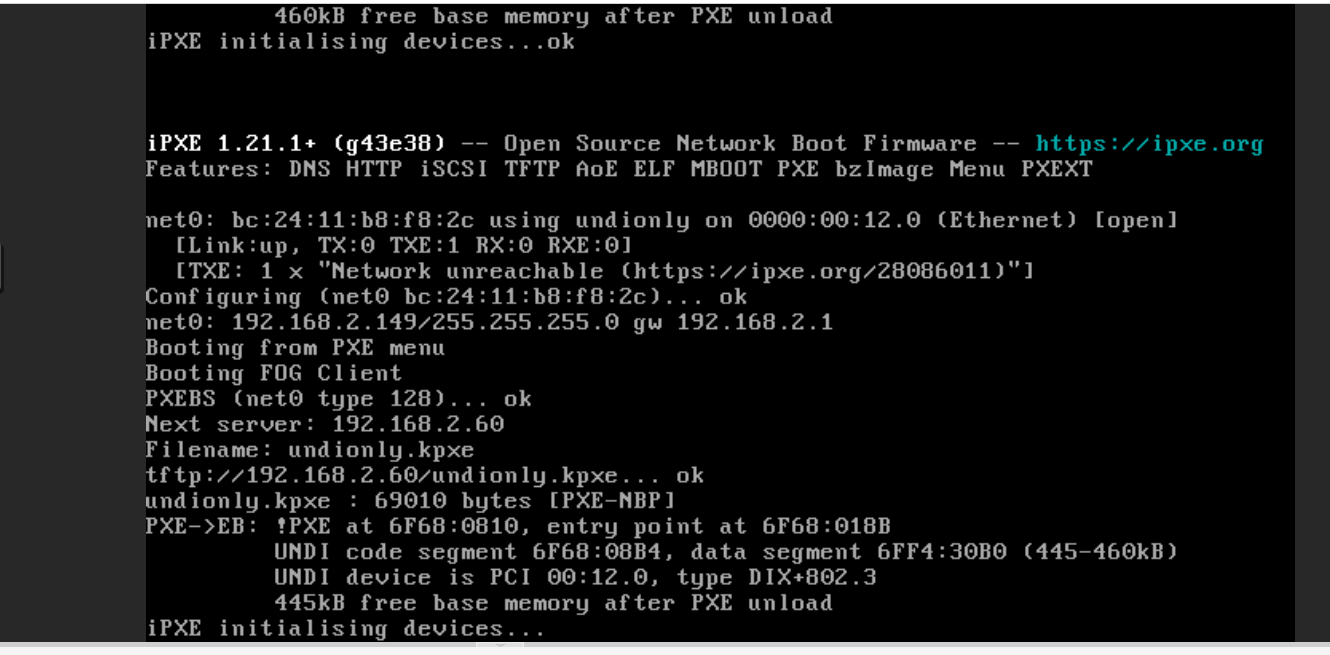
-
@45lightrain Are you running this environment on virtual box? The pxe boot messages don’t look typical FOG pxe boot messages.
So what device is 192.168.2.60?
Lets find out what actors are at play here. I have a tutorial to use the fog server to monitor the pxe booting process. You can run this from the fog server, but I think since you have dnsmasq running some place else, run the probe from that server. I want to capture the proxydns request on port 4011. That is unicast messaging so we need to capture that from the dnsmasq server’s perspective.
https://forums.fogproject.org/topic/9673/when-dhcp-pxe-booting-process-goes-bad-and-you-have-no-cluehttps://forums.fogproject.org/topic/9673/when-dhcp-pxe-booting-process-goes-bad-and-you-have-no-clue
I think there is more going on that we currently know.
-
Hey! I really appreciate you helping me out!
Sorry for the late response I made this a few minutes before heading to work and I gave the wrong IP for my DHCP server.
All of this except my router is being hosted on VMs through Proxmox.Right now my Pihole is acting as my DHCP server at IP “192.168.2.60”
IP “192.168.2.120” was my DNSMASQ server. I have turned this VM off due to the fact I was not able to tell if I was configuring it right.Right now I have
Pihole as my DHCP at IP 192.168.2.60
Fogserver at IP 192.168.2.91I have followed your guide and collected some packets on both my fogserver and pihole while the test system powered on and attempted to PXE boot on it.
from port 67
[
piholeoutput.pcap
fogserveroutput.pcap
]from port 4011
[
fogserverport4011.pcap
piholeport4011.pcap
]I have been staying up late trying to get this fog server set up for almost a week now, if you are not able to see what I am doing wrong I am extremely open to erasing all my VMs and starting from scratch, these VMs don’t have important data on them.
I have attached new updated images of what my current configuration is on my Pihole.
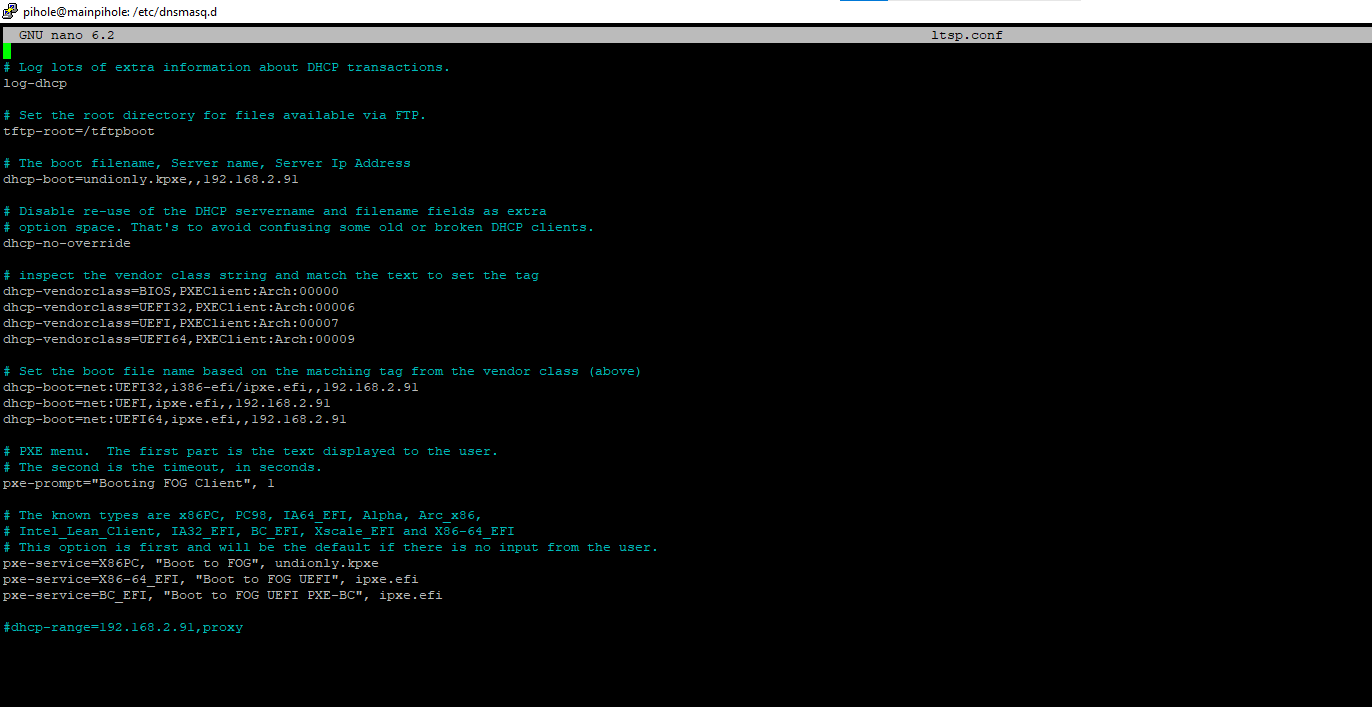
Here is a quick run down of how I have set up my current configuration.
After creating a new VM I installed Pihole, from there I went to the web console and enabled the DHCP server option.
I disabled the DHCP server option on my router as well.
I then went to /etc/dnsmasq.d and created ltsp.conf
I used the file format and settings from herehttps://docs.fogproject.org/en/latest/installation/network-setup/proxy-dhcp/#dns-masq-ltsp-settings
Afterwards I installed tftp on the pihole server using the commands from the highly voted comment.
https://askubuntu.com/questions/201505/how-do-i-install-and-run-a-tftp-serverI then downloaded the undionly.kpxe file to the root /tftp folder from here
https://ipxe.org/howto/chainloadingAfterwards, I created a new VM to install fog using this guide
https://docs.fogproject.org/en/latest/installation/server/install-fog-server/#final-stepsI then also installed tftp on this server and repeated the same process I did on pihole.
The fog server VM also has the undionly.kpxe file in /tftpUnfortunately, I do not recall what I selected for each of the prompts during the install but I can roll back to the snapshot of the VM I have prior to the install if needed.
-
@45lightrain The pcaps show confusion. Its not your dnsmasq configuration at the moment but more something going on with the pihole dhcp.
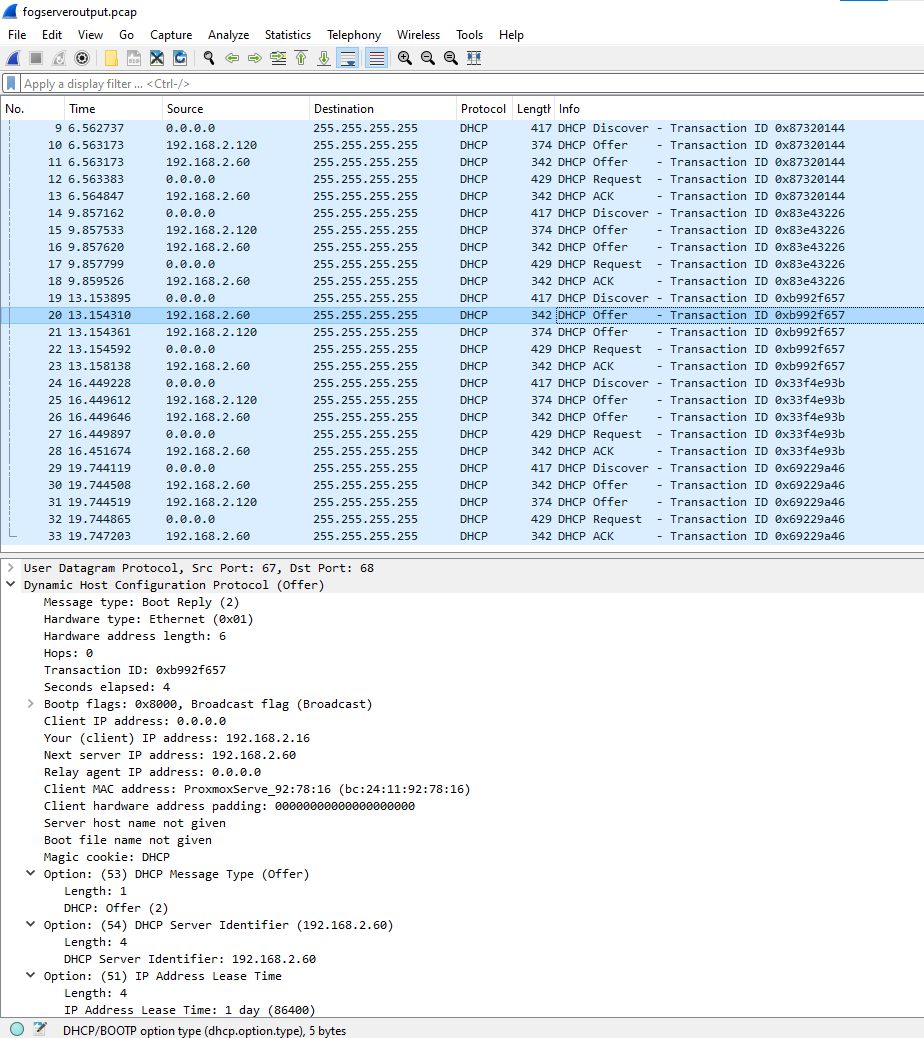
The pcap captured from the fog server -67 is what I would expect as a normal DORA process. Initially the pihole didn’t respond to the first DISCOVER packet but it did for the subsequent ones.
As expected from a soho router its posting that its the PXE boot server.That’s not a problem because your dnsmasq server has also sent an OFFER packet saying its a ProxyDHCP server. It completes the Request and Ack bits of DHCP and then 3 seconds later it restarts the process over again. This bit is strange.
Looking at the puhole pcap this one doesn’t align with what the fog server saw. This one only shows the pihole in response without the OFFER from dnsmasq AND the pihole server is now sending out the proper next server (fog server) and boot file names (!!) AND its saying it is the ProxyDHCP server (!!) It would have worked except that it said it was a proxydhcp server, because it failes on the next step.
The fog server 4011 is expected since ProxyDHCP is unicast messaging and not broadcast like dhcp.
The pihole 4011 is the proxyDHCP packet, but now the pihole is back saying its the next server (pxe boot) and not your FOG server.
-
@george1421
Just to clarify My Pihole is saying it is the ProxyDHCP server which is why the system is trying to boot to the pihole IP?Is pihole still considered a ProxyDHCP if it’s the only DHCP server/service in this network?
I do not believe this Pihole VM has dnsmasq installed as I tried restarting the dnsmasq service.So to clarify on the packet situation, this current setup has Pihole sending out the correct information but it’s also saying it is the proxyDHCP so when the fog server receives those requests it’s sending back offer packets with Pihole as the next server?
Do you know what could be overriding the ltsp.conf in the pihole server and directing packets to itself?
-
@45lightrain Lets cover a few things that I’m aware of that might help you get to the bottom of the issue.
- When you have a ProxyDHCP server and normal dhcp server on your network you will get two dhcp OFFERS. Well I guess it would be the same if you had two dhcp server you would see two offers, but that is a bit off point. You can tell if an OFFER packet is a proxy dhcp packet because dhcp option 60 will be set to PXEClient in the ProxyDHCP OFFER. That is a signal to the pxe booting client to come back and ask about pxe booting from the ProxyDHCP server. The pxe booting client will ignore the pxe boot information from the main dhcp server.
- A properly formed dhcp packet will have both the fields in the header {next-server} and {boot-file} filled out for the bootp booting protocol part of the protocol AND should have dhcp option 66 and 67 set for the dhcp booting protocol. Both must be filled out because its up to the pxe booting client to pick either the dhcp or bootp protocol.
- Your ltsp files are correct. The last one you posted has the dhcp-range… commented out, that turns off the proxydhcp feature in dnsmasq.
SO if you have a pihole server that runs dnsmasq, why are you running an external dnsmasq server. Does your pihole server have pxe boot options? I know pfsense has built in pxe boot fields you can fill out that supports dynamic (bios/uefi) boot loaders.
When trying to debug this wireshark/tcpdump is your friend that tells you what is flying down the wire. Just remember that dhcp is based on broadcast messages so you can “hear” them from any network port, and proxyDHCP like other unicast messages must be captured at the source, destination, or via a mirrored port.