FOG compatibility with Secure Boot on?
-
I haven’t seen anything regarding this, so I figured I’d ask. Will FOG ever work with Secure Boot on? I’ve been reading that Windows 11 will require secure boot, and that causes some issues. If FOG won’t support Secure Boot enabled, I may have to look at a different deployment solution. I would love to stay with FOG as it works for what I need.
If there is a way to make it work with secure boot enabled that I’m not aware of, please feel free to share what I need to do.
-
@yeet While I can’t speak for the developers, but there are no plans that I know of to support secure booting.
With that said while its not complicated to support secure booting, there is some expense involved. Both iPXE and FOS Linux kernels would need to be signed with a microsoft certificate or a matching signed certificate would need to be loaded into the target computer uefi firmware. Many linux distros have a shim boot loader that is signed by microsoft then their shim will only boot their kernel that matches their internal signed certificate. Its kind of complicated to explain, but the point is, its a bit more complicated to support secure booting, than just saying we support secure booting. There is also a cost involved with getting your OS certified as “safe for booting”. For a FOSS application that may be a high bar to get over.
-
@Yeet Currently FOG does not support secure boot as George said already. Though this has been discussed here a few times and I think one user even has worked out his own solution. Search the forums.
-
@george1421
This worry me about this news for Windows 11.
Is it the end of FOG to deploy Windows in the next year. I hope not -
@yeet @george1421 @Sebastian-Roth
Need to test it again, there are a lot of time that I test it, but the uefi firmware takes de capabilty to add trusted files, so, i you add the efi files to that database you can boot the pc from that file and continue using fog
the most of the problem is to update the .efi files
take this as example, when i can i try it again to certify it
-
@eduardotseoane Would you be able to explain what you did in detail?
I’d like to stay with FOG as well, but if I can’t get it to work with Secure Boot I’ll have to move to a different product completely
-
@sebastian-roth I haven’t been able to find a solution in the forums. When will FOG support secure boot? We need this to happen, or we will have to stop using FOG altogether.
-
@yeet said in FOG compatibility with Secure Boot on?:
When will FOG support secure boot?
As soon as someone is dare enough to get into it. I am definitely not the one. FOG is open source and anyone can work on it.
While I have not looked into this in detail it seems like there are several different ways of getting this to work - here are some pointers for you:
https://forums.fogproject.org/post/121630
https://forums.fogproject.org/post/128841 -
@yeet you must enroll the hash file from de UEFI interface; mok manager is capable to trust on 2 ways,
1º.- MOK can trust on files by hash when you enroll the file by de firmware interface, if you want you can send me the motherboard/pc manual and i can see if i can help to explain how you can do it.
2º.- I know, but i dont know how by the moment, that an efi application can be signed by a developer, (selfsigned or not), and the ca or ca intermediate can be added to the certificate database of efi firmware, to validate the file and that can be used…
3º.- I’m not sure, I’m studing about, but i think that you can do all from mok manager on uefi shell, or with some efi aplication designed for that.I’m sure that all this is possible, but I’m searching information about how can be do it…
some references that I’m reading are:https://www.rodsbooks.com/efi-bootloaders/controlling-sb.html
https://media.defense.gov/2020/Sep/15/2002497594/-1/-1/0/CTR-UEFI-Secure-Boot-Customization-UOO168873-20.PDF
https://docs.microsoft.com/en-us/windows-hardware/manufacture/desktop/windows-secure-boot-key-creation-and-management-guidance
https://ubuntu.com/blog/how-to-sign-things-for-secure-boot
https://jfearn.fedorapeople.org/fdocs/en-US/Fedora_Draft_Documentation/0.1/html-single/UEFI_Secure_Boot_Guide/index.html
https://www.qualcomm.com/media/documents/files/secure-boot-and-image-authentication-technical-overview-v1-0.pdf -
@yeet
Take a look at this post -
unfortunately i do not have time to write up in detail step by step instructions but this is how i’ve done it:
follow this brilliant guide:
https://www.rodsbooks.com/efi-bootloaders/controlling-sb.htmlincluding “Securing Multiple Computers” section, once you’ve generated the “LockDown.efi”
copy LockDown.efi to ipxe folder on fog server (i’ve renamed mine to EnrollKeys.efi) then add the option to PXE Menu.
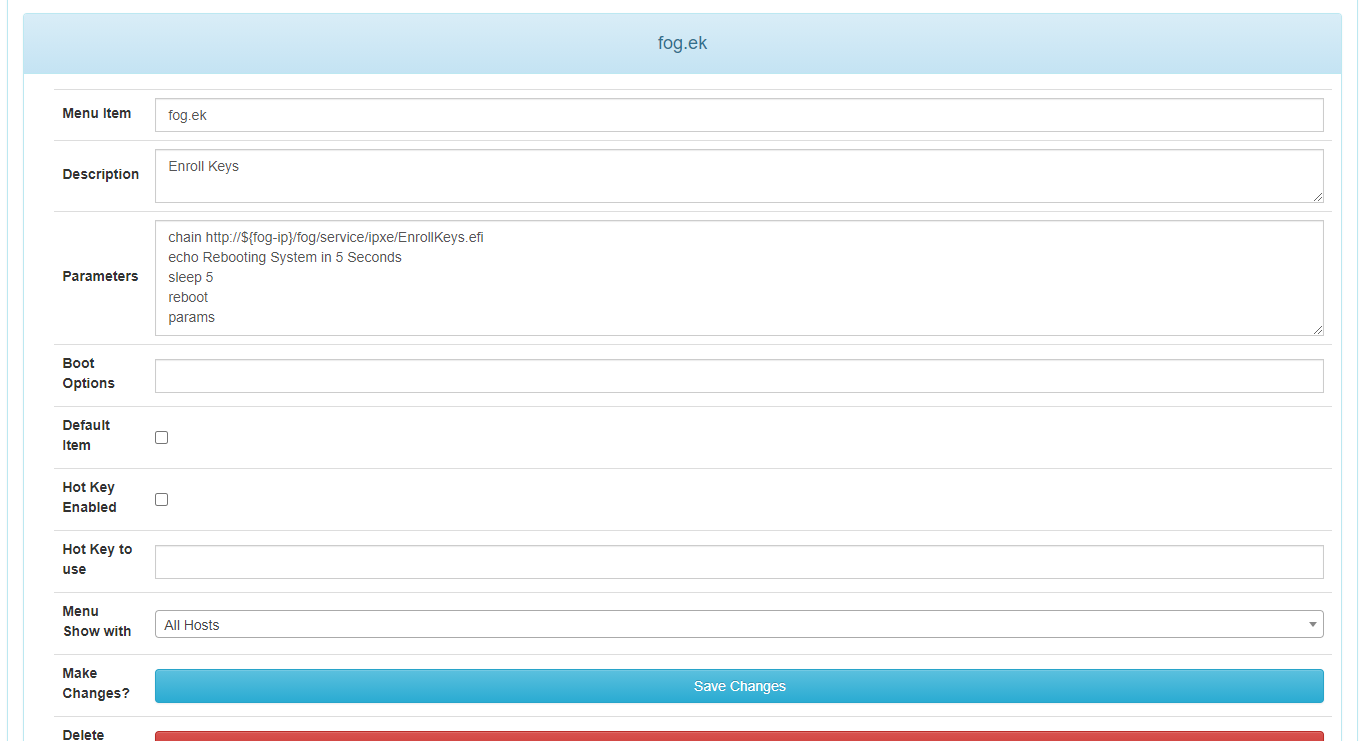
then sign your init, bzimage and any other bzimage version you may use with your new cert you’ve generated above - something like this:
cd /var/www/html/fog/service/ipxe mv bzImage bzImage-unsigned sbsign --key /etc/efikeys/DB.key --cert /etc/efikeys/DB.crt --output bzImage bzImage-unsigned mv bzImage32 bzImage32-unsigned sbsign --key /etc/efikeys/DB.key --cert /etc/efikeys/DB.crt --output bzImage32 bzImage32-unsigned mv bzImage41713m bzImage41713m-unsigned sbsign --key /etc/efikeys/DB.key --cert /etc/efikeys/DB.crt --output bzImage41713m bzImage41713m-unsignedjust remember to re-sign any init/bzimage when upgrading kernel/fog.
so the process is when you get a new machine put secureboot into user/setup mode then boot to pxe and run “Enroll Keys” option on pxe menu which will set secureboot keys accordingly, the beauty of this is you will also only need to do this once on a machine and then you will have secureboot on working with fog, when you come to reimage that same machine secureboot will already be setup.
the only caveat i would say is i don’t know what the behaviour is going to be when the Microsoft UEFI CA expires in 2026 - as you’re now effectively managing your own secureboot keys - you will need to update and manage the CAs in the db. this would normally be managed by microsoft updates/OEMs i assume.
-
We have find a workaround who works at now.
For Dell or HP in BIOS need to active Secure Boot in “Audit Mode” or “Client Keys”.
This is not secure but allow to use FOG Pxe and Windows 11.
Hope stay like this in the future
-
@florent All the uefi systems need to be in custom/setup/user mode to add keys or file hashes, the hint is to implement an adequate security level…
-
@sebastian-roth
Maybe a future solution for FOG project ?
iPXE secure boot : https://2pintsoftware.com/pricing/ -
Well, first of all … I’m sorry for getting up this old post.
Secondly … I’ve been reading some posts on this forum … and I’ve found this one which I think it’s very interesting to be linked in here (not sure if you’ve linked it yet, but I’d say I can’t see the link anywhere).
After researching a little bit more about this topic … I’ve found this project … which not sure if it could be interesting also. What do you think? Could this make easier the process described in @george1421’s tutorial?
Thank you guys, and so sorry again because I’ve created a new topic instead replying in here
 maybe some mod can remove it
maybe some mod can remove it 