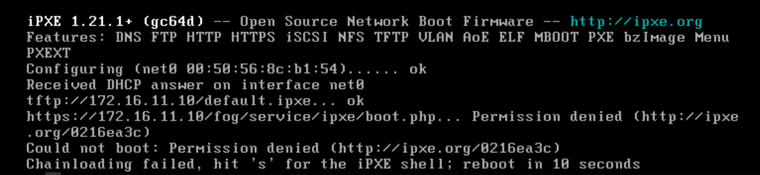
iPXE Boot issue: boot.php... Permission denied.
-
I did not notice a resolution here: Re: iPXE Boot issue : boot.php permission denied
We are using:
OS: Ubuntu 20.04
Fog: 1.5.9
This is using custom certs. If I run the installer with -S the self-signed certs work. If I use our custom certs then we get this permission denied error. We followed the steps outlined here: https://wiki.fogproject.org/HTTPS#Custom_CA_and_certificates.From the WebUI the custom certs are have been verified, in use.
-
@fmohammed And you ran the steps to rebuild the ipxe binaries?
Based on the permission denied, I am more suspect that the user who owns the file is root:root, which would explain why you’re seeing the permission denied error.
I would suggest by starting to run:
chown -R www-data:www-data /var/www/fog # to ensure even the custom srvpublic.crt and ca.cert.pem are owned by apache2 user for pass on chown -R www-data:fogproject /var/www/fog/service/ipxeThis will adjust the files so that permissions are back to that of the web user for ubuntu (apache2) and the fog user to allow you to download new kernels.
I don’t know that this will guarantee this will work, but it surely will not hurt.
-
@fmohammed @Tom-Elliott The permission denied error in iPXE/HTTPS context usually means it can’t validate the certificate.
Did you get any error when running
./buildipxe.sh /var/www/html/fog/management/other/ca.cert.pem?Edit: Hmm, looking at the iPXE version header (
gc64d) it seems like a properly compiled version of iPXE using a quite new commit from 15th of July (https://github.com/ipxe/ipxe/commits/master).Sure you put the certificate and CA files into the right places? Please run the following commands and post output here:
openssl x509 -noout -fingerprint -md5 -in /opt/fog/snapins/ssl/CA/.fogCA.pem openssl x509 -noout -fingerprint -md5 -in /var/www/html/fog/management/other/ca.cert.pem openssl x509 -noout -modulus -in /var/www/fog/management/other/ssl/srvpublic.crt | openssl md5 openssl rsa -noout -modulus -in /opt/fog/snapins/ssl/.srvprivate.key | openssl md5 openssl verify -verbose -CAfile /opt/fog/snapins/ssl/CA/.fogCA.pem /var/www/fog/management/other/ssl/srvpublic.crt -
@tom-elliott yes, we followed the steps to rebuild the ipxe binaries.
I did run the commands you had suggested above, but before I executed them I checked the ownership permissions on the folders.
The ipxe folder was fogproject:www-data. After executing your command the folder ownership was www-data:fogproject. but to no avail on my custom certs machine.
I have a machine with a clean install (./install_fog -S -y), I confirmed that the ipxe folder ownership was fogproject:www-data there as well, and that works.
On my separate machine with my custom certificates and recompiled PXE, one thought here is along with my custom certificates, do I need to include the custom roots and intermediates for the certificate in the recompile? As these custom certificates are generated off of public sector roots. Is it because these are not the standard commercial roots, the pxe client may not be able to connect?
-
@sebastian-roth here you go
- openssl x509 -noout -fingerprint -md5 -in /opt/fog/snapins/ssl/CA/.fogCA.pem
MD5Fingerprint=7A:C9:95:CF:19:D7:00:8C:D5:8F:77:B2:F2:D7:B8:4
- openssl x509 -noout -fingerprint -md5 -in /var/www/html/fog/management/other/ca.cert.pem
MD5Fingerprint=FF:05:F6:08:15:8D:8F:36:D1:CF:18:B1:28:83:B1:76
- openssl x509 -noout -modulus -in /var/www/fog/management/other/ssl/srvpublic.crt | openssl md5
(stdin)= 53f0d7c1e5003ae86e747066c87e8034
- openssl rsa -noout -modulus -in /opt/fog/snapins/ssl/.srvprivate.key | openssl md5
(stdin)= 53f0d7c1e5003ae86e747066c87e8034
- openssl verify -verbose -CAfile /opt/fog/snapins/ssl/CA/.fogCA.pem /var/www/fog/management/other/ssl/srvpublic.crt
The first line contains the org and the CN = <the FQDN of the machine>
error 20 at 0 depth lookup: unable to get local issuer certificate
error /var/www/fog/management/other/ssl/srvpublic.crt: verification failed -
@fmohammed said in iPXE Boot issue: boot.php... Permission denied.:
do I need to include the custom roots and intermediates for the certificate in the recompile? As these custom certificates are generated off of public sector roots. Is it because these are not the standard commercial roots, the pxe client may not be able to connect?
While it’s not an issue that your root is not one of the commercial ones, what you said might still be a good hint on why this is causing a problem.
In the default configuration, iPXE trusts only a single root certificate: the “iPXE root CA” certificate. This root certificate is used to cross-sign the standard Mozilla list of public CA certificates.
In the default configuration, iPXE will therefore automatically trust the same set of certificates as the Firefox web browser.
For that reason the
buildipxe.shis adding a different trust CA cert - the one given as parameter when calling the script. Usually the CA cert generated by the FOG installer but as you use your custom CA and cert (copied to that path) it’s using that.To make a long story short, I think the intermediate certificate is missing in the trust chain! Try calling it like this:
./buildipxe.sh /var/www/html/fog/management/other/ca.cert.pem,/var/www/html/fog/management/other/intermediate.pem(comma separated list of CA certs)Make sure you also add those intermediate CA cert to your Apache configuration manually.
-
@sebastian-roth Thanks, we gave that a go and now there is an error with the chainloading failing. So progress from denied.
Researching the error on ipxe (3e11623b) the error seems to be based on the lack of a DNS server. Currently these custom certs don’t have the IP address of the fog server as part of the certificate SAN, so we’re going to see if a certificate with the SAN containing the IP and hostname resolves this error.