FOG API question
-
Hello @JJ-Fullmer , hope all is well.
First of all, thanks for creating that Powershell module for FOG to be used via Powershell.
I have a question in regards to the script I’ve been using for a while. In it has the API for both the user and the FOG server.I want to be more secure in the sense of not putting the API in the script. I tried Microsoft’s module Secret Management and I can store both api keys under 2 different secrets. Here is the link from Microsoft: https://learn.microsoft.com/en-us/powershell/utility-modules/secretmanagement/get-started/using-secretstore?view=ps-modules
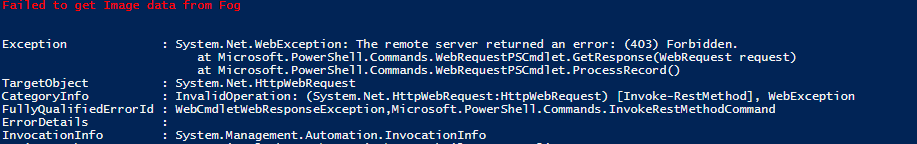
But when I try to retrieve the secrets, I get the 403 forbidden message.
Powershell variables for the both api keys for example:
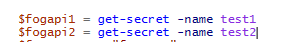
Error message:
It will only work if I add -asplaintext for example:
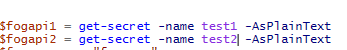
It won’t take the System.Security.SecureString
I double checked to make sure I’m using the correct fog and user api keys, but no dice.
Is there a way to secure these API keys instead of putting them directly in the Powershell script and also not doing the command -asplaintext?If anyone has suggestions, please let me know.
-
Ok,
I finally figured this out. I know it’s not the best method, but I prefer this than having the wording “plain text” Here’s what I did in case someone needs to do the same.
I read that API tokens do not go well as a securestring. Here are some references:
https://jamesone111.wordpress.com/2020/04/10/transformers-for-powershell-parameters-which-take-secrets/, and https://github.com/Azure/azure-powershell/issues/25533.So in order to get past this, I needed to create another variable as show below:
- $testapi1 = [pscredential]::new(“token”,$yourtoken)
You’re basically adding the pscredential above like you’re going to setup a username, but you put something like “token” or any wording as a placeholder for the username, then put the token in.
- Then after you define the header you do something like this: $testheader.add(fog-user-token’,$testapi1.GetNetworkCredential().password)
Again it’s not the best method, but I also read a way when you do read-host -aseecurestring and save your api there as a variable, you can dispose that variable so it doesn’t stay in memory.
$test.disposeof
If someone has any better ideas, please let me know as I’m always on here learning new things and want to share as well. This basically can be closed out.