Invalid signature detected on new PCs
-
Hi,
we got a few new pcs and I wanted to get them in FOG too. But with the same BIOS settings as the old pcs I’m getting the following error: Secure Boot Violation. Invalid signature detected. Check Secure Boot Policy in Setup.
The weird thing is: Nearly all options are the same the few different things are (old is the system where FOG is working):
Operating system: Windows 10 (old) - Windows 11 (new)
Mainboard: Gigabyte Z690 UD (old) - Gigabyte Z790 AORUS ELITE AX (new)
BIOS version: F7b (03/28/2022) (old) - F10 (12/25/2023) (new)All other things are the same as far as I can see. The factory setting of the Secure Boot was on Custom instead Standard but with neither of the both option the PC can’t load FOG. Our FOG version is 1.5.9 and following my information this version should be working with Secure Boot as it does on the old PCs.
Does anyone knows what the problem could it be?
-
@sega FOG doesn’t have a signed shim/bootable binaries, not by default, so if you had this in the past, I don’t know how you did it but it would seem your new systems have overridden the certificates on the machines themselves which need your “old” certificates placed back on them to allow the booting sequence to successfully operate.
-
@Tom-Elliott Thanks for you quick reply.
As far as I know (didn’t installed it) there weren’t any certificates installed.
And, as I read my first post, that could cause a confusion, the old systems still work. So we have both systems currently here and just the old PCs working with the settings. -
@sega FOG doesn’t do secure boot out of the box, we just don’t
If your old machines are using FOG with Secure Boot Enabled, you need to install the certificates for those boot files on the new machines as well.
-
@Tom-Elliott I know when we set up the last Pcs we didn’t install any certificates, just changed some settings in the mainboard and thats it (plus updating the BIOS).
Can you tell me where the certificates could be? Then I could look if there are some on the FOG server. -
@sega It sounds more like you really disabled “secure” boot while maintaining UEFI boot?
-
@Tom-Elliott I thought that too but these are the settings from the old PCs. The only thing that is weird here, is that Secure boot is enabled but there is also a “Not active”?
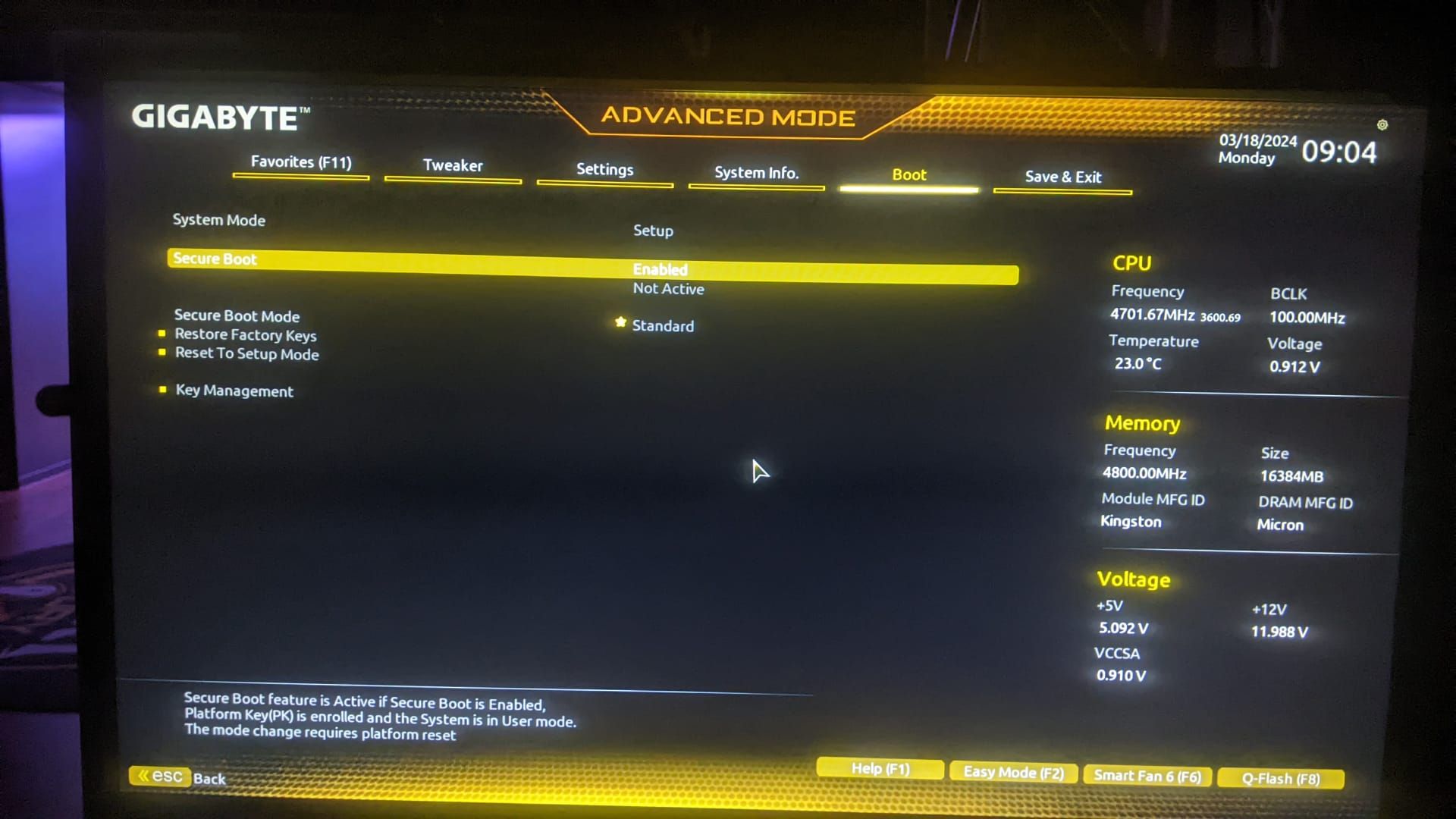
-
@sega Based on what I can tell, somebody installed the certificates on these machines. How I couldn’t tell you.
Our files are not shimmed by us so I cannot tell you what was or wasn’t done. All I know is if secure boot is enabled (as it appears) then somebody manually installed the certificates to ensure it was able to work in a secure boot mode.
-
@Tom-Elliott Hmm ok, thats really weird. I did the set up for these machines and if they won’t installed with the FOG client,I can’t imagine how… Can you tell me where normally the certificates are?
I found some certificates in following folder but I don’t think that’s the right ones… “opt -> fog -> snapins -> ssl -> CA” but I guess that something complete different -
@sega I think what Tom is referring to is something like this tutorial: https://forums.fogproject.org/topic/15888/imaging-with-fog-and-secure-boot-poc
Also like Tom said the FOG Project doesn’t sign either iPXE or the FOS Linux kernel that is beyond the scope of the FOG Project. So if you must have secure boot enabled then you must do something like in the above tutorial, create your own private certificates and upload them to the uefi firmware, then sign ipxe.efi, snp.efi, snponly.efi and bzImage with your custom certificate. Then a computer with secure boot enabled will “trust” the FOG imaging process. Without the FOG Project boot files being singed, your computer will reject them and not boot.
-
After many try&error runs, I managed to sign the files and to boot into the FOG menu with secure boot enabled. And I can deploy an image, register the host and do all the other things except boot from hard disk. Whenever I choose this option in the FOG menu he just goes back into the menu.
When I boot directly from the hard disk it works and also if I disable the secure boot option the FOG menu can boot from hard disk.What could be the problem here? Oh and while I was troubeshooting I updated Ubuntu from 20.04 to 22.04 and FOG to 1.5.10