UEFI/BIOS Coexistence Help
-
@george1421 Finally figured it out. I feel like an absolute idiot, but I’m blaming Microsoft for a big portion of it.
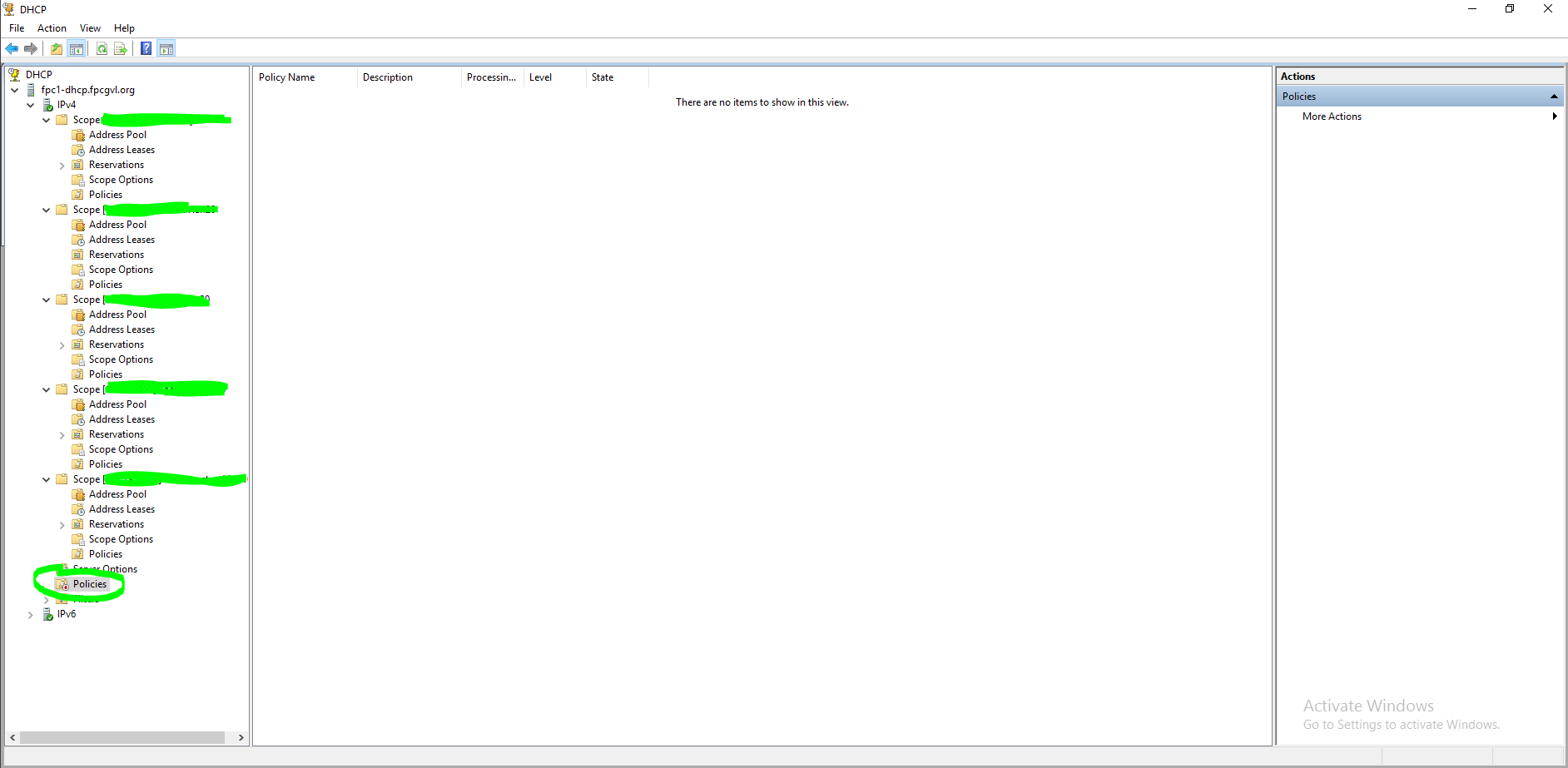
The “Policies” under IPv4 MUST be enabled, even if there are no policies under that folder. That fixed the problem completely.
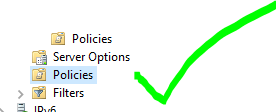
By default, this was disabled, and since I did not have policies in that particular folder, I did not see the need to enable it.
-
@mrawesome987 that is crazy obsecure, but I’m glad you found it.
This sounds like a perfect tip to add to the wiki @Wayne-Workman