Chainloading failed, hit 's' for the iPXE shell
-
Afternoon guys, another small glitch. undionly.kpxe, fog 1.5.10.1662.
This is a
System Manufacturer Hewlett-Packard
System Product HP Pro3500 Series
System Version
System Type Type: Desktop
BIOS Vendor AMI
BIOS Version 8.16
BIOS Date 07/17/2013
Motherboard Manufacturer Foxconn
Motherboard Product Name 2ABF
Motherboard Version 3.20
Motherboard Serial Number
Motherboard Asset Tag
CPU Manufacturer Intel Corporation
Corporation
CPU Version Intel Pentium
Pentium CPU G2030 @ 3.00GHz
CPU G2030 @ 3.00GHz
CPU Normal Speed Current Speed: 3000 MHz
CPU Max Speed Max Speed: 3800 MHz
Memory 3.73 GiB
Hard Disk Model SanDisk SSD PLUS 240GB
Hard Disk Firmware UF4004RL
Chassis Manufacturer Hewlett-Packard
Chassis Version
Chassis Serial
Chassis Asset CZC3457Z0Z
GPU-0 Vendor Intel Corporation
GPU-0 Product Xeon E3-1200 v2/3rd Gen Core processor Graphics ControllerI have several of these - about 15 - and all seem ok. This one and 2 others give me the following error upon pxe boot:
GATEWAY IP: 192.168.3.253 Auto-select: Boot to FOG BOOT SERVER IP: 192.168.0.48 PXE->EB: !PXE at 9944:0078, entry point at 9944:0100 UNDI code segment 9944:32CC, data segment 8CFA:C4AG@ (563-626kB) UNDI device is PCI 63:00.6, type DIX+802.3 563KB free base memory after PXE unload iPXE initialising devices... iPXE 1.21.1+ (g5deSd) -- Open Source Network Boot Firmware -- https://ipxe.org Features: DNS FTP HTTP HTTPS iSCSI NFS TFTP VLAN AoE ELF MBOOT PXE bzImage Menu PXEXT Configuring (net0 20:44:fd:14:dd:f6)...... ok Received DHCP answer on interface net0 tftp://192.168.3.253/default.ipxe.... Connection timed out (https://ipxe.org/4c126835) Chainloading failed, hit 's' for the iPXE shell; reboot in 18 seconds_Hitting ‘s’ and then entering “autoboot” continues with the boot process, into fog, and no more issues. Why would this happen ?
-
I have the impression this issue has something to do with DHCP server in the gateway competing with proxydhcp in the fog server.
I have updated DHCP settings in Unifi to allow / block DHCP traffic (DHCP Guarding). I have included FOG’s dhcppxory address and seems to be working ok now.
-
@lperoma So I can make the generalization statement that
timefixes your issue?What I want you to test is this.
PXE boot into the error and then press s to get to the ipxe console.
Wait 20 seconds.
Now key in the following at the console prompt
chain tftp://192.168.3.253/default.ipxe
Does this work and continue into the FOG iPXE menu. In that the only thing different between not working and working is time? (I’m driving to a point here).If time fixes the issue, lets place a dumb switch (unmanaged cheap-o like monoprice) switch between the building network switch and the target computer. Now pxe boot the computer does it boot correctly? If yes then its possibly a spanning tree issue with your building network switch. Make sure your building switch has fastSTP, portfast or whatever your switch mfg calls the fast spanning tree protocol. I might be off base here but it sounds like it might be spanning tree. I know that processor is pretty old, but I don’t think its cpu related.
-
@george1421 I will give it a try.
However what does not make sense is 192.168.3.253 is my gateway (and DHCP server). No TFTP there, I wonder if this is a default “try to TFTP the gateway when everything else fails”.
Infrastructure has RSTP, but I wonder how could this affect an endpoint, there only one connection to it.
I have dnsmasq on 192.168.0.40, and Fog on 192.168.0.21.
Do you want me to chain into dnsmaq or fog ?
Thanks,
-
@lperoma said in Chainloading failed, hit 's' for the iPXE shell:
192.168.3.253
What device is that (manufacturer and model)? is that a soho router?
How does dnsmasq fit into this design? Is it setup as a proxy dhcp server?
The reason why I ask is I’ve seen many soho routers say (tell client computers) they are the boot server even if you have dhcp option 66 set correctly. The bios on the target computer is getting ipxe loaded correctly. Once iPXE starts it issues a dhcp discovery request again to find the boot server’s IP address. What it is getting this time is your gateway’s address.
With this new information I don’t think its spanning tree.
-
@george1421 Ubiquiti UDM pro.
I removed the TFTP / netowrk boot options from it as it can only send one pxe file, and these days there’s a good mix of BIOS & EFI, so I had to install dnsmasq in a dhcpproxy config, which seems to be working away nicely.
This is a successful boot of a BIOS machine and this is the conversation with the dhcpproxy:
2024-10-16T10:20:06+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 available DHCP subnet: 192.168.0.0/255.255.252.0 2024-10-16T10:20:06+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 vendor class: PXEClient:Arch:00000:UNDI:002001 2024-10-16T10:20:06+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 user class: iPXE 2024-10-16T10:20:06+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 PXE(eth0) 52:54:00:92:d1:4a proxy 2024-10-16T10:20:06+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 tags: BIOS, eth0 2024-10-16T10:20:06+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 bootfile name: undionly.kpxe 2024-10-16T10:20:06+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 next server: 192.168.0.21 2024-10-16T10:20:06+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 broadcast response 2024-10-16T10:20:06+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 sent size: 1 option: 53 message-type 2 2024-10-16T10:20:06+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 sent size: 4 option: 54 server-identifier 192.168.0.40 2024-10-16T10:20:06+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 sent size: 9 option: 60 vendor-class 50:58:45:43:6c:69:65:6e:74 2024-10-16T10:20:06+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 sent size: 17 option: 97 client-machine-id 00:d0:37:b8:0d:ce:18:53:49:a0:87:9c:05:d0... 2024-10-16T10:20:06+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 sent size: 50 option: 43 vendor-encap 06:01:03:08:07:80:00:01:c0:a8:00:28:09:0e... 2024-10-16T10:20:07+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 available DHCP subnet: 192.168.0.0/255.255.252.0 2024-10-16T10:20:07+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 vendor class: PXEClient:Arch:00000:UNDI:002001 2024-10-16T10:20:07+0000 proxydhcp dnsmasq-dhcp[1288]: 3246548343 user class: iPXE 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 0 available DHCP subnet: 192.168.0.0/255.255.252.0 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 0 vendor class: PXEClient 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 0 user class: iPXE 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 0 PXE(eth0) 192.168.3.79 52:54:00:92:d1:4a undionly.kpxe 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 0 tags: eth0 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 0 bootfile name: undionly.kpxe 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 0 next server: 192.168.0.40 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 0 broadcast response 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 0 sent size: 1 option: 53 message-type 5 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 0 sent size: 4 option: 54 server-identifier 192.168.0.40 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 0 sent size: 9 option: 60 vendor-class 50:58:45:43:6c:69:65:6e:74 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 0 sent size: 17 option: 97 client-machine-id 00:d0:37:b8:0d:ce:18:53:49:a0:87:9c:05:d0... 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 0 sent size: 28 option: 43 vendor-encap 47:04:80:00:00:00:0a:13:01:42:6f:6f:74:69... 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-tftp[1288]: sent /tftpboot/undionly.kpxe to 192.168.3.79 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 available DHCP subnet: 192.168.0.0/255.255.252.0 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 vendor class: PXEClient 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 user class: iPXE 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 PXE(eth0) 52:54:00:92:d1:4a proxy 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 tags: eth0 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 bootfile name: undionly.kpxe 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 next server: 192.168.0.21 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 broadcast response 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 sent size: 1 option: 53 message-type 2 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 sent size: 4 option: 54 server-identifier 192.168.0.40 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 sent size: 9 option: 60 vendor-class 50:58:45:43:6c:69:65:6e:74 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 sent size: 17 option: 97 client-machine-id 00:d0:37:b8:0d:ce:18:53:49:a0:87:9c:05:d0... 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 sent size: 50 option: 43 vendor-encap 06:01:03:08:07:80:00:01:c0:a8:00:28:09:0e... 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 available DHCP subnet: 192.168.0.0/255.255.252.0 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 vendor class: PXEClient 2024-10-16T10:20:24+0000 proxydhcp dnsmasq-dhcp[1288]: 1516823406 user class: iPXEThis is a conversation of the failing PXE boot on another BIOS machine:
2024-10-16T10:48:48+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 available DHCP subnet: 192.168.0.0/255.255.252.0 2024-10-16T10:48:48+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 vendor class: PXEClient:Arch:00000:UNDI:002001 2024-10-16T10:48:48+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 PXE(eth0) 2c:44:fd:14:dd:f6 proxy 2024-10-16T10:48:48+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 tags: BIOS, eth0 2024-10-16T10:48:48+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 bootfile name: undionly.kpxe 2024-10-16T10:48:48+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 next server: 192.168.0.21 2024-10-16T10:48:48+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 broadcast response 2024-10-16T10:48:48+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 sent size: 1 option: 53 message-type 2 2024-10-16T10:48:48+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 sent size: 4 option: 54 server-identifier 192.168.0.40 2024-10-16T10:48:48+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 sent size: 9 option: 60 vendor-class 50:58:45:43:6c:69:65:6e:74 2024-10-16T10:48:48+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 sent size: 17 option: 97 client-machine-id 00:74:5b:5b:52:eb:1a:0b:93:db:13:37:77:0b... 2024-10-16T10:48:48+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 sent size: 50 option: 43 vendor-encap 06:01:03:08:07:80:00:01:c0:a8:00:28:09:0e... 2024-10-16T10:48:56+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 available DHCP subnet: 192.168.0.0/255.255.252.0 2024-10-16T10:48:56+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 vendor class: PXEClient:Arch:00000:UNDI:002001 2024-10-16T10:48:59+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 available DHCP subnet: 192.168.0.0/255.255.252.0 2024-10-16T10:48:59+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 vendor class: PXEClient:Arch:00000:UNDI:002001 2024-10-16T10:48:59+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 PXE(eth0) 192.168.2.47 2c:44:fd:14:dd:f6 undionly.kpxe 2024-10-16T10:48:59+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 tags: BIOS, eth0 2024-10-16T10:48:59+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 bootfile name: undionly.kpxe 2024-10-16T10:48:59+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 next server: 192.168.0.40 2024-10-16T10:48:59+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 sent size: 1 option: 53 message-type 5 2024-10-16T10:48:59+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 sent size: 4 option: 54 server-identifier 192.168.0.40 2024-10-16T10:48:59+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 sent size: 9 option: 60 vendor-class 50:58:45:43:6c:69:65:6e:74 2024-10-16T10:48:59+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 sent size: 17 option: 97 client-machine-id 00:74:5b:5b:52:eb:1a:0b:93:db:13:37:77:0b... 2024-10-16T10:48:59+0000 proxydhcp dnsmasq-dhcp[1288]: 4279557622 sent size: 28 option: 43 vendor-encap 47:04:80:00:00:00:0a:13:01:42:6f:6f:74:69... 2024-10-16T10:49:00+0000 proxydhcp dnsmasq-tftp[1288]: error 0 TFTP Aborted received from 192.168.2.47 2024-10-16T10:49:00+0000 proxydhcp dnsmasq-tftp[1288]: sent /tftpboot/undionly.kpxe to 192.168.2.47 2024-10-16T10:49:00+0000 proxydhcp dnsmasq-tftp[1288]: sent /tftpboot/undionly.kpxe to 192.168.2.47 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 available DHCP subnet: 192.168.0.0/255.255.252.0 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 vendor class: PXEClient:Arch:00000:UNDI:002001 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 user class: iPXE 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 PXE(eth0) 2c:44:fd:14:dd:f6 proxy 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 tags: BIOS, eth0 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 bootfile name: undionly.kpxe 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 next server: 192.168.0.21 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 broadcast response 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 sent size: 1 option: 53 message-type 2 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 sent size: 4 option: 54 server-identifier 192.168.0.40 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 sent size: 9 option: 60 vendor-class 50:58:45:43:6c:69:65:6e:74 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 sent size: 17 option: 97 client-machine-id 00:74:5b:5b:52:eb:1a:0b:93:db:13:37:77:0b... 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 sent size: 50 option: 43 vendor-encap 06:01:03:08:07:80:00:01:c0:a8:00:28:09:0e... 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 available DHCP subnet: 192.168.0.0/255.255.252.0 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 vendor class: PXEClient:Arch:00000:UNDI:002001 2024-10-16T10:49:07+0000 proxydhcp dnsmasq-dhcp[1288]: 4202889309 user class: iPXEConnection timed out (https://ipxe.org/4c126835)
Chainloading failed,hit ‘s’ for the iPXE shell; reboot in 18 seconds_
enter ‘autoboot’ and then …
2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 available DHCP subnet: 192.168.0.0/255.255.252.0 2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 vendor class: PXEClient:Arch:00000:UNDI:002001 2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 user class: iPXE 2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 PXE(eth0) 2c:44:fd:14:dd:f6 proxy 2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 tags: BIOS, eth0 2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 bootfile name: undionly.kpxe 2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 next server: 192.168.0.21 2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 broadcast response 2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 sent size: 1 option: 53 message-type 2 2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 sent size: 4 option: 54 server-identifier 192.168.0.40 2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 sent size: 9 option: 60 vendor-class 50:58:45:43:6c:69:65:6e:74 2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 sent size: 17 option: 97 client-machine-id 00:74:5b:5b:52:eb:1a:0b:93:db:13:37:77:0b... 2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 sent size: 50 option: 43 vendor-encap 06:01:03:08:07:80:00:01:c0:a8:00:28:09:0e... 2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 available DHCP subnet: 192.168.0.0/255.255.252.0 2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 vendor class: PXEClient:Arch:00000:UNDI:002001 2024-10-16T10:50:03+0000 proxydhcp dnsmasq-dhcp[1288]: 1083364685 user class: iPXE 2024-10-16T10:50:04+0000 proxydhcp dnsmasq-dhcp[1288]: 0 available DHCP subnet: 192.168.0.0/255.255.252.0 2024-10-16T10:50:04+0000 proxydhcp dnsmasq-dhcp[1288]: 0 vendor class: PXEClient 2024-10-16T10:50:04+0000 proxydhcp dnsmasq-dhcp[1288]: 0 user class: iPXE 2024-10-16T10:50:04+0000 proxydhcp dnsmasq-dhcp[1288]: 0 PXE(eth0) 192.168.2.47 2c:44:fd:14:dd:f6 undionly.kpxe 2024-10-16T10:50:04+0000 proxydhcp dnsmasq-dhcp[1288]: 0 tags: eth0 2024-10-16T10:50:04+0000 proxydhcp dnsmasq-dhcp[1288]: 0 bootfile name: undionly.kpxe 2024-10-16T10:50:04+0000 proxydhcp dnsmasq-dhcp[1288]: 0 next server: 192.168.0.40 2024-10-16T10:50:04+0000 proxydhcp dnsmasq-dhcp[1288]: 0 broadcast response 2024-10-16T10:50:04+0000 proxydhcp dnsmasq-dhcp[1288]: 0 sent size: 1 option: 53 message-type 5 2024-10-16T10:50:04+0000 proxydhcp dnsmasq-dhcp[1288]: 0 sent size: 4 option: 54 server-identifier 192.168.0.40 2024-10-16T10:50:04+0000 proxydhcp dnsmasq-dhcp[1288]: 0 sent size: 9 option: 60 vendor-class 50:58:45:43:6c:69:65:6e:74 2024-10-16T10:50:04+0000 proxydhcp dnsmasq-dhcp[1288]: 0 sent size: 17 option: 97 client-machine-id 00:74:5b:5b:52:eb:1a:0b:93:db:13:37:77:0b... 2024-10-16T10:50:04+0000 proxydhcp dnsmasq-dhcp[1288]: 0 sent size: 28 option: 43 vendor-encap 47:04:80:00:00:00:0a:13:01:42:6f:6f:74:69... 2024-10-16T10:50:04+0000 proxydhcp dnsmasq-tftp[1288]: sent /tftpboot/undionly.kpxe to 192.168.2.47 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 available DHCP subnet: 192.168.0.0/255.255.252.0 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 vendor class: PXEClient 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 user class: iPXE 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 PXE(eth0) 2c:44:fd:14:dd:f6 proxy 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 tags: eth0 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 bootfile name: undionly.kpxe 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 next server: 192.168.0.21 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 broadcast response 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 sent size: 1 option: 53 message-type 2 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 sent size: 4 option: 54 server-identifier 192.168.0.40 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 sent size: 9 option: 60 vendor-class 50:58:45:43:6c:69:65:6e:74 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 sent size: 17 option: 97 client-machine-id 00:74:5b:5b:52:eb:1a:0b:93:db:13:37:77:0b... 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 sent size: 50 option: 43 vendor-encap 06:01:03:08:07:80:00:01:c0:a8:00:28:09:0e... 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 available DHCP subnet: 192.168.0.0/255.255.252.0 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 vendor class: PXEClient 2024-10-16T10:50:05+0000 proxydhcp dnsmasq-dhcp[1288]: 2900218228 user class: iPXEI wonder if the line :
2024-10-16T10:49:00+0000 proxydhcp dnsmasq-tftp[1288]: error 0 TFTP Aborted received from 192.168.2.47
is the culprit of the problem, or else something else.
-
@lperoma TBH I never look at the DORA process from the server side because it only tells us half the story. It looks like its working right in both flows.
Are you sure the dnsmasq is configured on the .40 server as a dhcp proxy or is it doing traditional dhcp functions. In a dhcp proxy config it only sends the boot file override command and then at the end of the DORA process it will then answer the dhcp proxy request on port 4011. Your dnsmasq configuration should look similar to the one in this tutorial: https://forums.fogproject.org/topic/12796/installing-dnsmasq-on-your-fog-server
When I try to debug this process I use the process outlined in this document: https://forums.fogproject.org/topic/9673/when-dhcp-pxe-booting-process-goes-bad-and-you-have-no-clue
Since your dnsmasq server isn’t on your FOG server, I would run the tcpdump command from your dnsmasq server since there is some unicast communications to dnsmasq you would miss if you ran it on the fog server. It would be intersting to see what the client is being told on the pxe booting process that fails.
Minus the dhcp proxy communications you would miss you could also use wireshark with the capture filter of
port 67 or port 68running on a witness computer on the same IP subnet as the pxe booting target computer. There may be an unknown dhcp server mucking up the works on this pxe booting.If you are willing to share the pcap I will look at it to see if there is anything that jumps out at me as the problem.
-
@george1421 output2.pcap output.pcap
there you go.
output.pcap is a successful boot.
output2.pcap is a bad boot that required ‘hit s’ and then ‘autoboot’Thanks for checking this
-
@lperoma Thank you for the pcaps. There is something strange going on here.
This is what I gleaned from our discussion (actors)
192.168.0.40 is dnsmasq 192.168.3.253 is my gateway (and DHCP server). 192.168.0.21 Fog Server 192.168.0.0/255.255.252.0 /23 networkWhen I look at the pcap the target computer 192.168.3.8 is downloading undionly.kpxe from the dnsmasq server 0.40 and not the fog server 0.21. At no time in the pcap do I see 0.21 in the dialog. Also it looks like the target computer is on a different subnet than the dhcp server and fog server. The pcap only shows one side of the conversation. I can see the Discover and Request bits of DORA. I’m missing what the dhcp server(s) are telling the target computer. This is because the client is on the other side of some router. The target computer is indeed a bios base system (HP) and the 0.40 server is running as a VM under proxmox.
So there are several questions here.
- Is your fog server really 192.168.0.21
- Why does the dnsmasq server have FOG’s pxe boot files? Those should be on the fog server.
- Why does dnsmasq only tell the client computer to boot from itself and not the fog server?
- You are capable of causing a good pxe boot and not good pxe boot. What are you doing different, or what is different between the two pcaps?
It would be interesting to see the other side (what the client is being told) by taking a third computer loaded with wireshark to the clients subnet and then use a capture filter of
port 67 or port 68to see what actors are involved and what the client is being told. At this time I’m only interested in what is not working.ref:
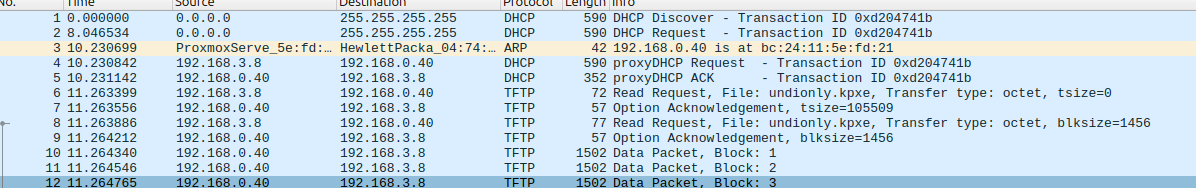
-
@george1421 Thanks so much.
A couple of notes for clarity.
Network: 192.168.0.0/255.255.252.0 -> /22 (not /23), thus the client is in the same subnet.
Fog server: 192.168.0.21
dnsmasq server: 192.168.0.40dnsmasq server (LXC CT) has a copy of /tftpboot from fog server. I wanted to run dnsmasq without interfering FOG. I hope this answers Qs 1-2-3.
re. Q4, I have no idea, further more, sometimes the same clients boots fine, some other times, it doesnt.
-
I have the impression this issue has something to do with DHCP server in the gateway competing with proxydhcp in the fog server.
I have updated DHCP settings in Unifi to allow / block DHCP traffic (DHCP Guarding). I have included FOG’s dhcppxory address and seems to be working ok now.
-
L lperoma has marked this topic as solved on