PXE-E32: TFTP open time out on palo alto dhcp server
-
FYI,
I have tried downloading “undionly.kpxe” whith this comand “tftp -i 192.168.96.204 get undionly.pxe” on my tftp windows client and it seems that I download it correctly.

Any idea? Thanks
-
@fernando-martinez Manual TFTP download on a Windows machine is a great test. Should have suggested that way earlier. Now we know TFTP is working.
Re-read the whole topic I noticed that we see
VMware, Inc.in one of the pictures. Can you tell us more about your setup? I guess you have VMware Workstation or ESXi server running and try to PXE boot from the FOG server. Can you please try some physical machine within your network as well? Just your normal Windows PC will do, reboot and select PXE boot as temporary first boot. This won’t cause any trouble on the PC. Just to see if this is booting to the menu. -
@Sebastian-Roth
We are trying on ESXI VM Machine, but we have the same problem whith a physical machine from my network.
We have another Fog Server on another networwk running correctly whith physicals and VM machines.
The only diference is the dhcp server, the first is Palo Alto and the other is Winows Server DHCP. -
@fernando-martinez There must be something we overlook here but I can seem to get it. You can manually download the file via Windows tftp command so it should work.
Would you please try to capture a network packet dump on your FOG server when this PXE issue happens so we see what is actually sent over the wire? https://forums.fogproject.org/topic/9673/when-dhcp-pxe-booting-process-goes-bad-and-you-have-no-clue
-
@Sebastian-Roth Collecting the pcap from a witness computer if the target is on a different vlan from the FOG server, or from the FOG server to get the best info if the target computer is on the same vlan as the FOG server.
@fernando-martinez if your target computer is on a different vlan than the fog server install wireshark on a witness computer and use the capture filter of
port 67 or port 68If the target computers is on the same subnet as the fog server then use the instructions in the tutorial.
Upload the pcap to a file share site (i.e. google drive, dropbox, etc) and share as public read. Either post the link here or DM either Sebastian or myself and we will look at the pcap and tell you what we see. Be sure to use the capture filter outlined so we do see things we shouldn’t in your packet capture.
-
@george1421 said in PXE-E32: TFTP open time out on palo alto dhcp server:
uter is on a different vlan than the fog server install

this is de output.pcap.
Fog Server: 192.168.96.204
Fog Client: 192.168.96.182The server and client are in the same Vlan.
Do you need more info?Thanks
-
https://www.dropbox.com/s/fn4b256v81ttvlg/output.pcap?dl=0
here is the pcap file.
-
@fernando-martinez I’ll be able to look at the pcap file in detail in a few minutes.
The first pass at it I see a problem. The client is asking for
undionly.kpxe.0which is an indication that you have a version of dnsmasq on your fog server that is older than version 2.75. Older versions than that always appended .0 for some legacy reason. You should upgrade to a newer version of dnsmaq, but you can trick it by creating a sym link between undionly.kpxe.0 and undionly.kpxe in the/tftpbootdirectory. You will need to do the same for ipxe.efi to ipxe.efi.0 -
@fernando-martinez said in PXE-E32: TFTP open time out on palo alto dhcp server:
tftp -i 192.168.96.204 get undionly.pxe
Dnsmasq version is 2.75, I tried to create a sym link but i have the same problem.

-
@fernando-martinez would you grab another pcap with these links in place?
What I find strange is that why is it appending the .0 to the file name and why does it appear to request the file and appear to download it. From your picture of the pcap (it appears you deleted the original pcap) the client asks for the file size of undionly.kpxe.0 and it appears to get the file size because it asks for the file next from 96.204. If that file did not exist it should have not attempted to download it but fail on the file size request.
Edit: Ah I had the version wrong it needs to be 2.76 or later ref: https://forums.fogproject.org/topic/12796/installing-dnsmasq-on-your-fog-server
That config file “should” work with 2.75 but we will see the .0 file name appended onto the file name like we see in the pcap.
-
@fernando-martinez said in PXE-E32: TFTP open time out on palo alto dhcp server:
I tried to create a sym link but i have the same problem.
From the picture we see you created the symlinks in the fogproject source directory. You need to create thos in
/tftpboot/directory… -
Hello guys! we did it!!
I created sym link in /tftpboot directory and i’ts worked!!
Now we have to configure.
Many thanks for your help!!!
-
Hi,
I have the same problem, can u help me?
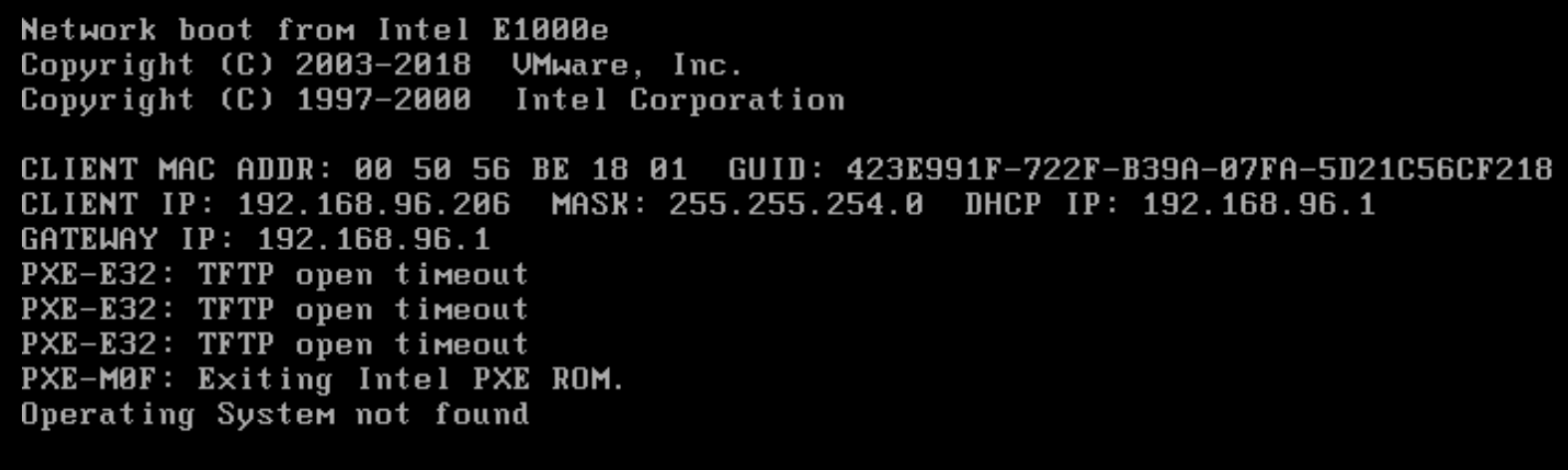
-
@joanmarzo Are you using a PaloAlto dhcp server too?
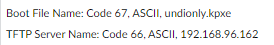
What specifically do you have defined for dhcp options 66 and 67?
-
-
@joanmarzo So I take it that 192.168.96.162 is the IP address of the fog server?
This is me just making an educated guess. Has the IP address of the fog server changed since FOG was installed? The fog server needs to be configured to use a static IP address before FOG is installed. As I said this is an educated guess but a FOG server IP address of .162 is pretty close to the IP address assigned to the target computer of .206. I might guess they are in the same subnet dhcp scope range. That is why I’m asking if the fog server ip address has changed.
-
@george1421 said in PXE-E32: TFTP open time out on palo alto dhcp server:
This is me just making an educated guess. Has the IP address of the fog server changed since FOG was installed? The fog server needs to be configured to use a static IP address before FOG is installed. As I said this is an educated guess but a FOG server IP address of .162 is pretty close to the IP address assigned to the target computer of .206. I might guess they are in the same subnet dhcp scope range. That is why I’m asking if the fog server ip address has changed.
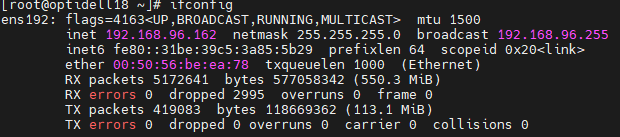
Yes, the IP of fogserver is 192.168.96.162 and I put it and static IP, If u want any information tell to me, thanks a lot
-
@joanmarzo Sorry about the slow response its been busy here this AM. So you put the static address in before you installed FOG? OK good. You can confirm that the IP address hasn’t changed between the time you installed FOG and now by inspecting the .fogsettings file
more < /opt/fog/.fogsettingsThere is an IP field in there that indicates the IP address when FOG was installed.If the IP address hasn’t changed then we might suspect your dhcp server is doing something abnormal. If we follow this thread it looks like we used dnsmasq to make everything work in the end.
I think in your case since you are using a firewall for a dhcp server and we’ve had issues in the past with firewalls not sending out the right information needed for pxe booting that we go ahead and install dnsmasq on your fog server. In this configuration the dnsmasq program will ONLY supply the pxe booting information all other information will still come from your main dhcp server. The nice thing about this is if you install dnsmasq on your FOG server and then turn off the fog server then all pxe booting will be turned off too.
If you follow these instructions you will be up and running with dnsmasq on your fog server in about 10 minutes. https://forums.fogproject.org/topic/12796/installing-dnsmasq-on-your-fog-server
If you have multiple subnets you will need to adjust an existing setting in your subnet router if you want to pxe boot on the subnets where your FOG server is not. Other than dealing with subnets, dnsmasq should just work. -
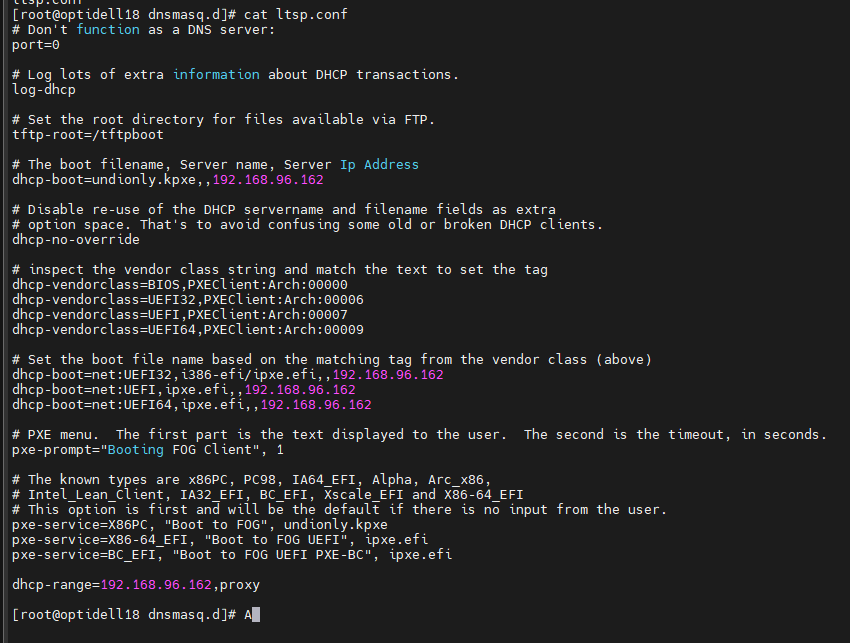
I do the dnsmasq but the fog doesn’t work, any idea? I paste an screenshot about the ltsp.conf
-
@joanmarzo Did you make sure that the dnsmasq service is running? It should appear here with this command
ps aux | grep dnsmasqIt should show you the service name and give you an ip address. If that doesn’t work make sure that you have the linux server firewall turned off. DNSMASQ is a simple tool, it should just work. Your ltsp.conf file looks good. It should just work.
If it not work then we can do some more deeper debugging. We are not out of options now.