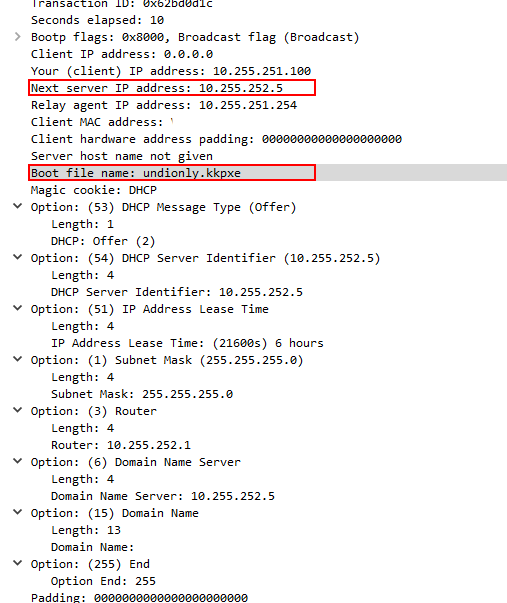
@george1421 said in Issue with EFI through PFSense Firewall:
Between next-server and class insert this line
option tftp-server-name 10.255.252.5;
Then for every instance of “filename…”; just below that line enter
option bootfile-name “<boot_file>”;
Where <boot_file> matches the boot file name issued by the filename command.
George,
Just wanted to take a moment to thank you for helping to troubleshoot this with me. 
I did as you requested.
if the “option tftp…” line is enabled the dhcp server will fail to start. Isn’t it the case for isc-dhcp-server that the “next-server …” line is the equivalent?
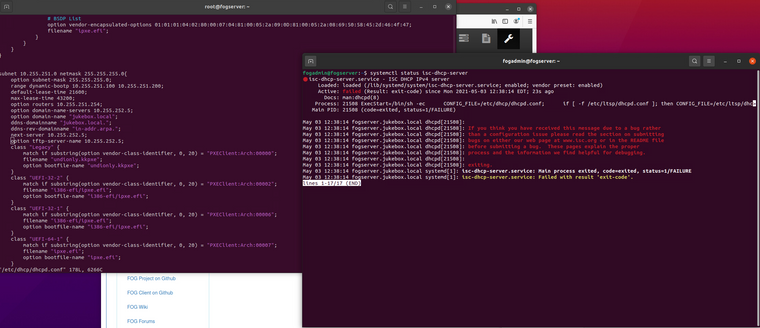
if I disable the next-server line and just use “option tftp” it also fails to start:
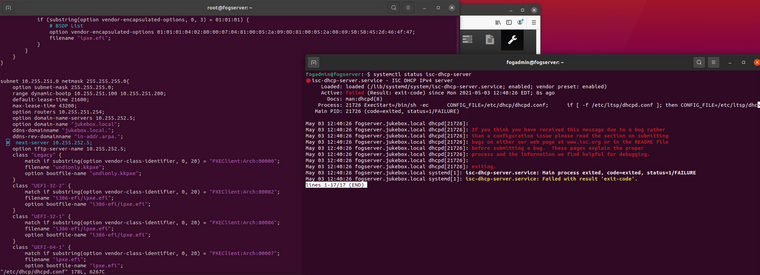
if I leave the “option boot-file…” lines in and leave “next-server…” on and “option tftp…” off, the server starts
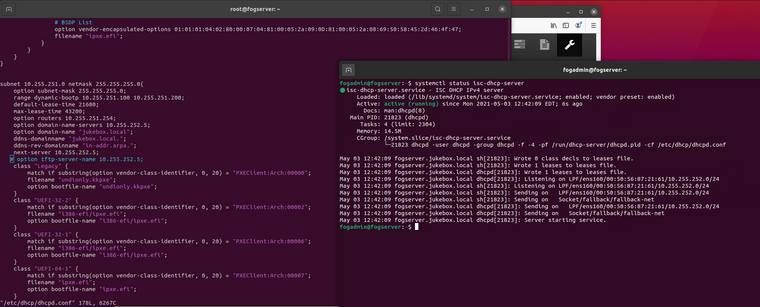
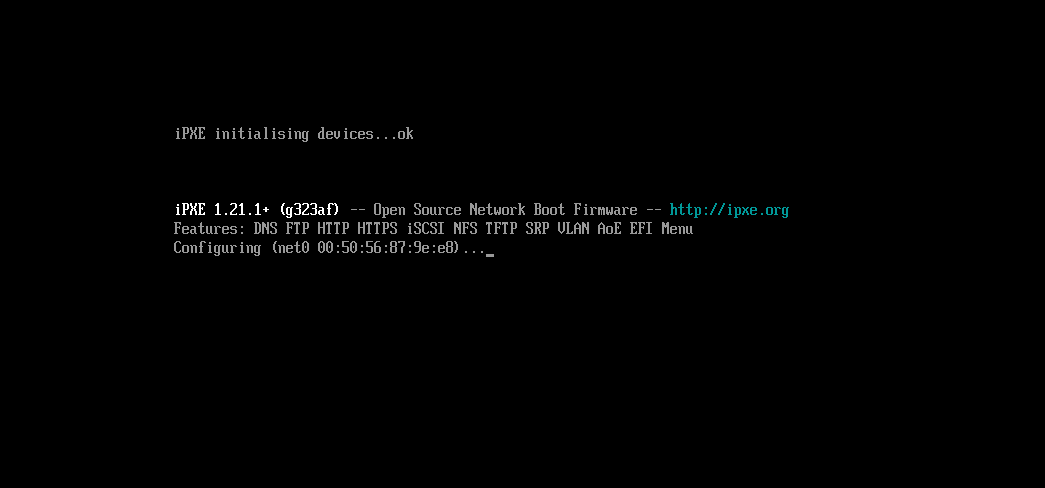
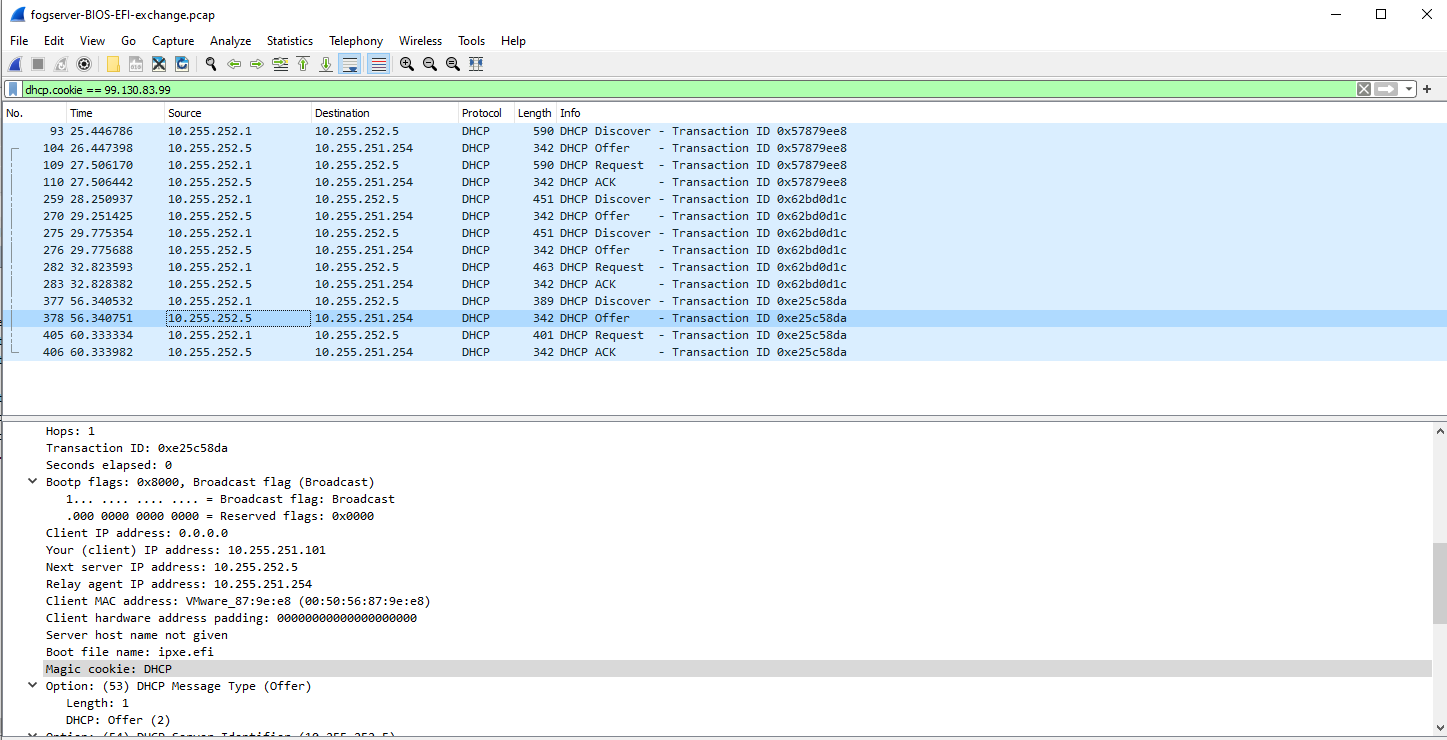
However there is no difference in boot either in a VM, or hardware. I did however snag this screenshot (sorry for the glare) from the laptop which might shed some light.
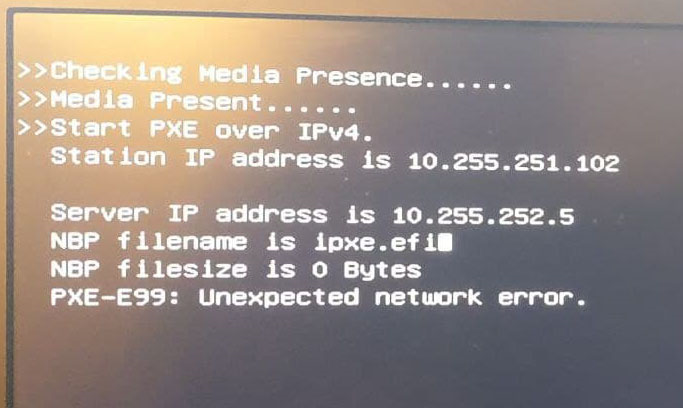
I then reverted my dhcpd.conf to without the changes you recommended and confirmed the same result, sans the square at the end of the filename. Still same PXE error.
So it appears that the dhcp exchange for EFI mode on the computers are happening, they are getting the right configuration data, but the data is getting mangled at some point.
Any thoughts?