NBP filesize is 0 Bytes; PXE-E18: Server response timeout
-
@foggymind Another note, I seem to be able to rename systems so communication with the fog client seems to be working.
-
@george1421 I ran tcpdump on the fog server and got the following results.
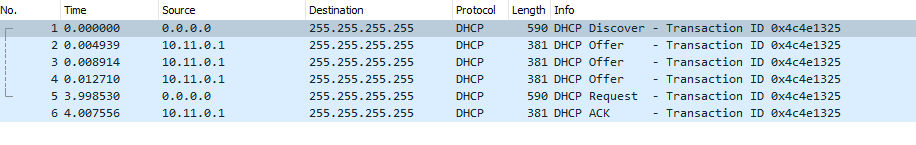
-
@foggymind What was your capture filter on the FOG sever? Was it according to the tutorial? https://forums.fogproject.org/topic/9673/when-dhcp-pxe-booting-process-goes-bad-and-you-have-no-clue
From the screen shot it looks strange in that there was a discover, then 3 offers from the dhcp server and then after 4 seconds the client sends the request. What is the target computer playing hard to get?
I would expect to see after that ACK, a query from the target computer to the FOG server asking for the file on udp port 69.
Make sure you have the proper capture filter. Once you have a good pcap upload it to a file share site and post the link here or IM me the link. I need to look into each packet to find out what is going wrong. From the picture it should be working.
-
I am wondering why we see three offers all coming from the very same IP. Is this the way Windows DHCP servers do this when they are in a sync pool?
@foggymind Would be helpful if you could save and upload a PCAP file from Wireshark so we can have a deeper look as well to be able to help. If you don’t want to post this to the public then send George and/or me a private message in the forum.
-
@george1421
Thanks for the quick reply!From the screen shot it looks strange in that there was a discover, then 3 offers from the dhcp server and then after 4 seconds the client sends the request. What is the target computer playing hard to get? – not sure!
Yes, I followed that tutorial, is there something else I need to do with the filters or just type in the command?
-
Hi
what is solution of the problem